Planning for P.I with Caroline Mouton
Executive Summary
‘Planning P.I. with Caroline Mouton’ focuses on data management and risk, covering topics such as privacy and data protection, Protection of Personal Information Act (POPIA) compliance and privacy risk management, compliance and risk management in data governance, and the importance of a business process register and risk assessment. Caroline Mouton discusses the risks associated with unlawful processing of personal information, data breaches, and compliance frameworks. She highlights the importance of compliance with positive obligations and risk management, personal information impact assessment, privacy impact assessment, and data protection legislation. The webinar concludes with a privacy and security program for 2024, privacy impact assessment, risk management and compliance, and risk assessment in the payroll system.
Webinar Details:
Title: Planning for P.I. with Caroline Mouton
Date: 15 March 2024
Presenter: Caroline Mouton
Write-up Author: Howard Diesel
Contents
Executive Summary.
Webinar Details:
Presentation on Data Management and Risk.
The Life of Pi and Data Management
Privacy and Data Protection.
Introduction to POPIA Compliance and Privacy Risk Management
Risks of Unlawful Processing of Personal Information.
Risks Associated with Data Breaches and Compliance Frameworks.
Compliance and Risk Management in Data Governance.
Data Protection and Compliance Frameworks.
Importance of Compliance with Positive Obligations and Risk Management
Importance of a Business Process Register and Risk Assessment
Personal Information Impact Assessment and Penalties in POPIA.
Privacy and Security Program for 2024.
Privacy and Security Program Planning.
Risk Management and Compliance.
Privacy Impact Assessment and Its Importance.
Privacy Impact Assessment and Data Protection Legislation.
Compliance Risk Monitoring Plan.
Risk Assessment in the Payroll System.
Presentation on Data Management and Risk
Caroline emphasises the importance of data management and privacy in a data steward role at FNB. She aims to provide insight into managing risk, particularly in relation to data management and systems design. Understanding risk is crucial for data management professionals as it influences design work, architecture, and active data management. A risk-based approach helps facilitate conversations with compliance management and risk managers and reduces the risk profile through effective management.
The Life of Pi and Data Management
Caroline shares her title, "The Life of Pi," relating the novel and shares how it relates to the life cycle approach to protecting personal information. Their work specialises in information governance, information risk, and compliance risk, focusing on restoring the data to data protection. Although they discuss privacy and legal obligations, they are not lawyers, and legal teams should interpret and implement their advice. The speaker appreciated the hosting organisation and mentioned a coaching platform for upscaling or accessing resources.
Figure 1 About Caroline Mouton
Figure 2 The New LinkedIn Page
Figure 3 Skill Coaching-as-a-Service
Privacy and Data Protection
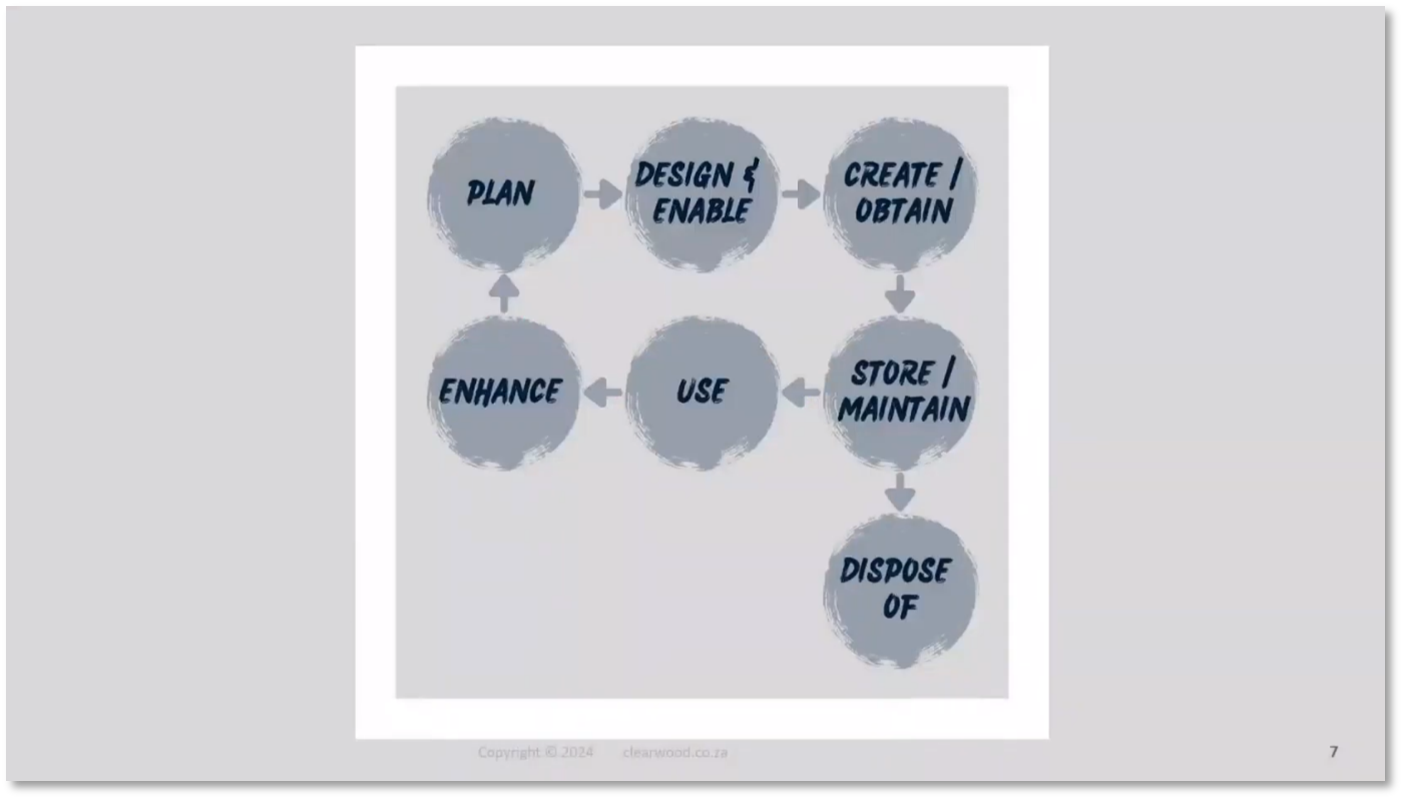
The key points in planning for the Protection of Personal Information Act (POPIA) are covered. The life cycle approach to data protection involves identifying role players in privacy, with the responsible party being the company making decisions about data collection and flow. The responsible party is accountable for the data of employees and customers, including the flow of personal data into third parties, such as outsourcing HR functions or hosting data in third-party data centres. Decisions regarding data management and flow also impact systems architecture and business analysis; thus, taming the tiger in your boat becomes essential. Providing skills coaching as a service to coach through the privacy and data protection journey can be helpful.
Figure 4 Data Lifecycle
Figure 5 POPIA Role Players
Introduction to POPIA Compliance and Privacy Risk Management
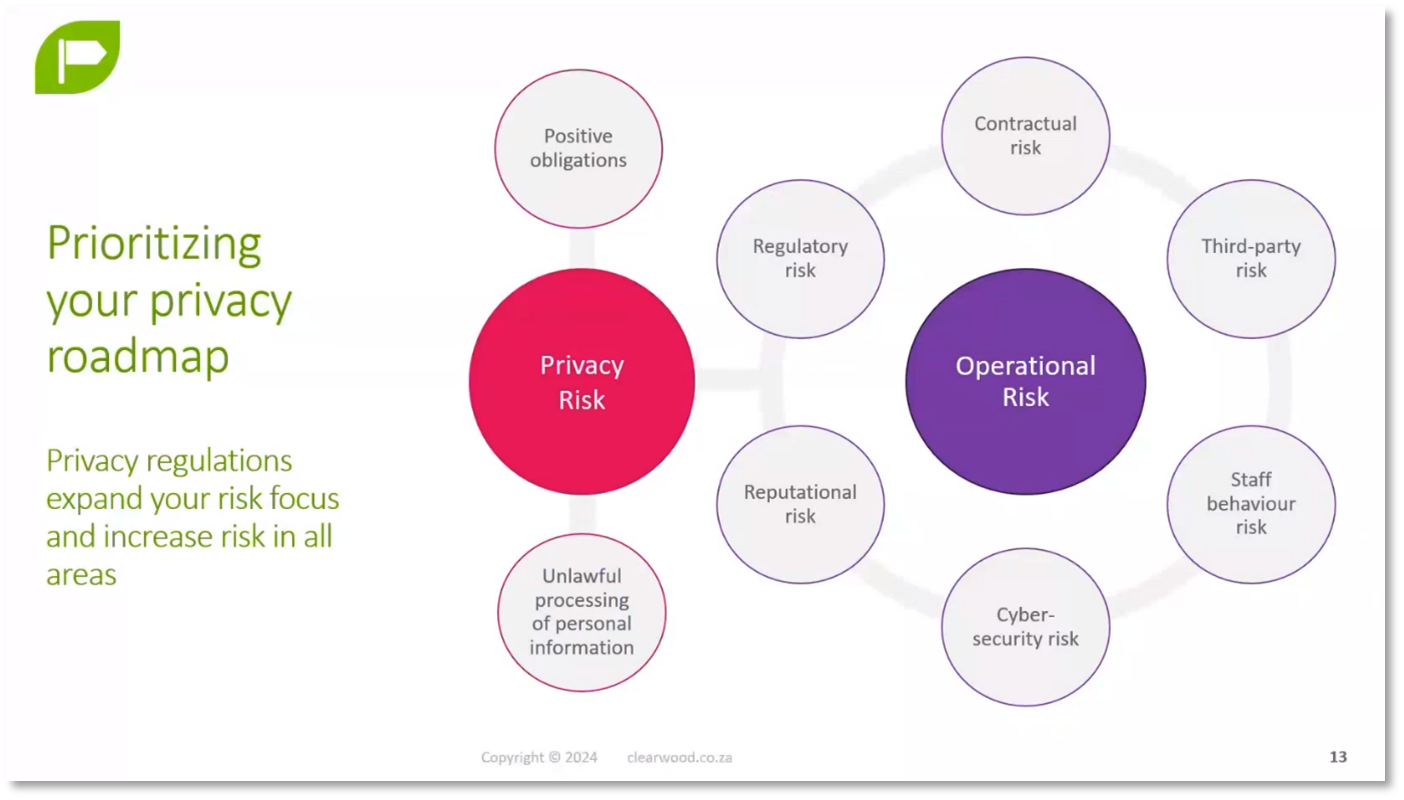
POPIA is a data privacy legislation that introduces an "information officer" role and new operators. The head of the organisation is the information officer, and individuals must register as information officers. POPIA emphasises the "riskiest risks" concept and encourages companies to manage privacy and other operational risks. Although it does not provide specific guidelines for managing risk, it requires companies to consider privacy and other risk types. Companies must identify their positive obligations by law, such as conducting privacy impact assessments, which are essential foundational tasks for data managers. The perspective presented in POPIA is that penalties help data managers identify important areas of focus rather than being seen as fear tactics.
Figure 6 Tip for how to use penalties to your advantage
Figure 7 Prioritizing your Privacy Roadmap
Risks of Unlawful Processing of Personal Information
It is illegal for companies to retain an individual's data without a valid reason. This retention may include sensitive information like health and financial data, even after the individual's contract with the company has ended. While regulatory compliance may require retaining certain data types, companies should be mindful of keeping unnecessary personal information. Organisations' governance, risk, and compliance functions focus on strategic, operational, financial, and reputational risks. Privacy and security risks, such as data breaches and corporate espionage, can have wide-reaching and serious consequences, including negative press and strategic risks.
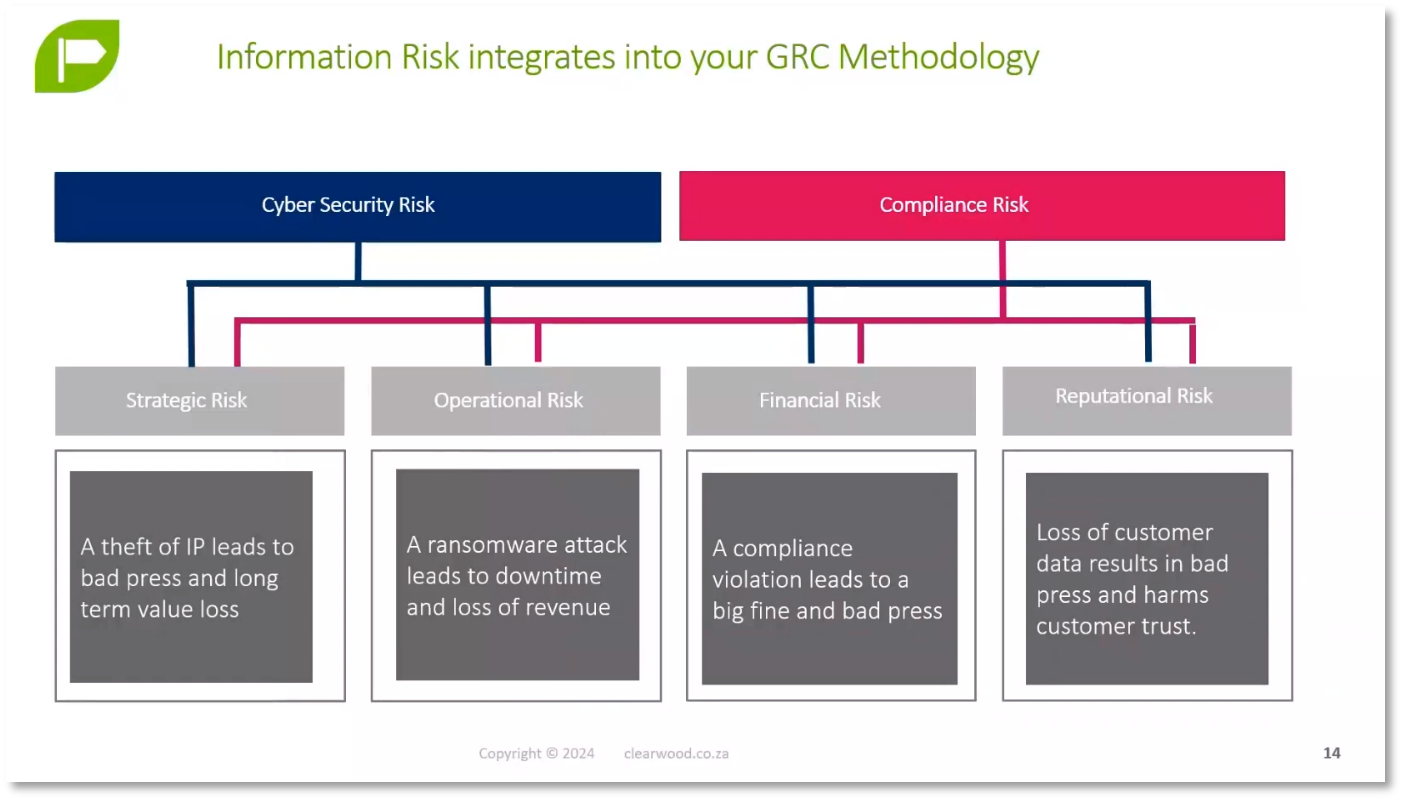
Risks Associated with Data Breaches and Compliance Frameworks
Operational risks in AI include ransomware attacks leading to downtime and revenue loss, while financial risks involve fines and bad press due to cybersecurity breaches or privacy non-compliance. Reputational risks arise when a company loses customers or fails to attract new ones due to data breaches or non-compliance with privacy laws. Compliance frameworks are essential to monitor data breaches and privacy non-compliance risks, as affected by codes of conduct such as the South African Direct Marketing Association's code for direct marketing. An enforcement notice was recently issued for a company's failure to comply with a data subject's request for removal from a mailing list, resulting in reputational damage.
Figure 8 Information Risk Integrates into your GRC Methodology
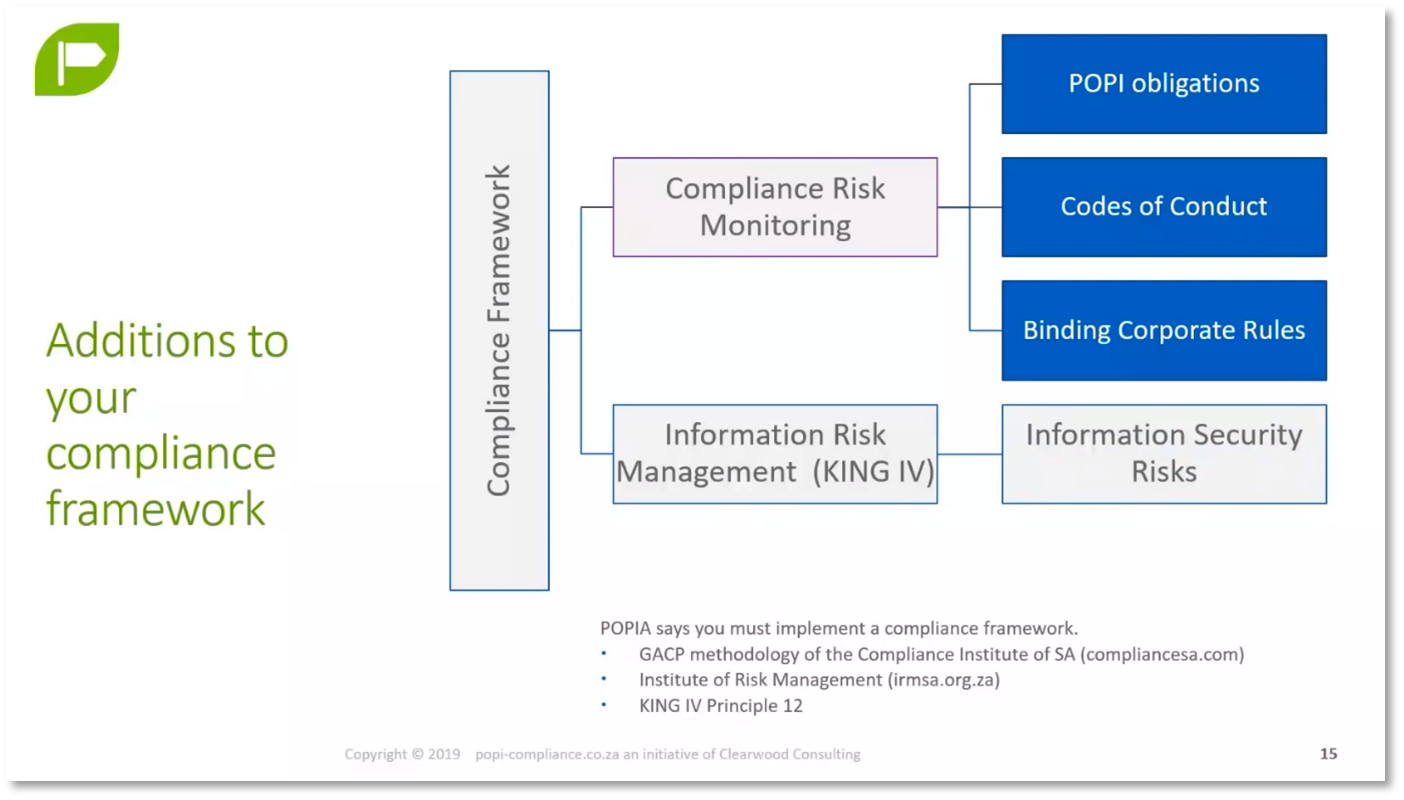
Figure 9 Additions to your compliance framework
Compliance and Risk Management in Data Governance
The Credit Bureau Association expects members to adhere to a code of conduct and binding corporate rules, which are crucial for compliance obligations, especially in large organisations with a global presence. Compliance obligations can extend to contracts and industry-specific legislations, requiring a thorough understanding of risk management and data governance. Key concepts include a compliance framework, risk register, and monitoring plan, which assesses the effectiveness of implemented mitigations in addressing the risks. Any significant changes in systems, data design, architecture, or partnerships can impact compliance risks, necessitating a reassessment of the risk monitoring plan. Moving into senior roles in data management and governance requires a comprehensive understanding of compliance and risk management in data governance, including assessing potential penalties and fines, reputational and financial risks, and the sensitivity of managed data.
Figure 10 Compliance Risk Management
Data Protection and Compliance Frameworks
Data management involves managing individual data subjects and their information through risk management methodology. Cybersecurity risks should be included in a risk register, and a compliance framework should be established to address these risks. The compliance framework outlines the policies, processes, and procedures necessary to comply with regulations such as ISO 27001 and DAMA-DMBoK, which provide best practices that inform the organisation's data protection and privacy policies. Internal policies on data protection outline organisational obligations and restrictions regarding personal information, as well as the associated risks. Procedures such as the Personal Information Impact Assessment (PIIA) are crucial for assessing the impact of changes on privacy obligations and the data subjects, producing a PIIA report as evidence of compliance.
Figure 11 GRC Lifecycle - How it all fits together
Importance of Compliance with Positive Obligations and Risk Management
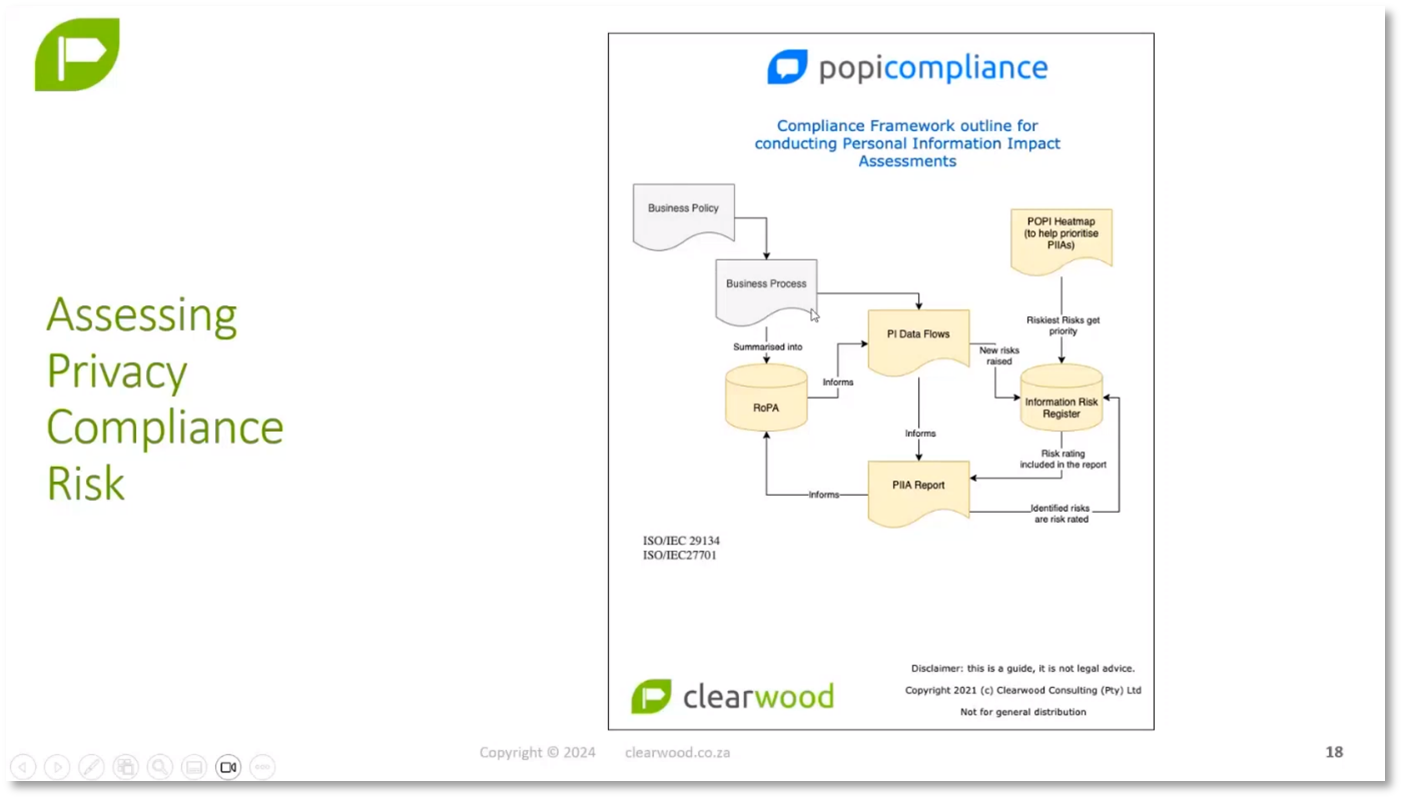
When a regulator launches an investigation of a company, compliance with positive obligations is crucial. A privacy report is necessary to provide evidence of compliance. Risk management is essential in demonstrating compliance and fits in the middle of the process. Business policies and processes result in data flows, which must be evaluated for risk. Privacy impact assessments are important for business analysts when designing new systems or software. Conducting a privacy impact assessment leads to a Privacy report, which informs the information risk register and helps evaluate the level of risk. The register of processing activity, also known as a ROPA, is crucial for managing the processing activities within an organisation.
Figure 12 Assessing Privacy Compliance Risk
Importance of a Business Process Register and Risk Assessment
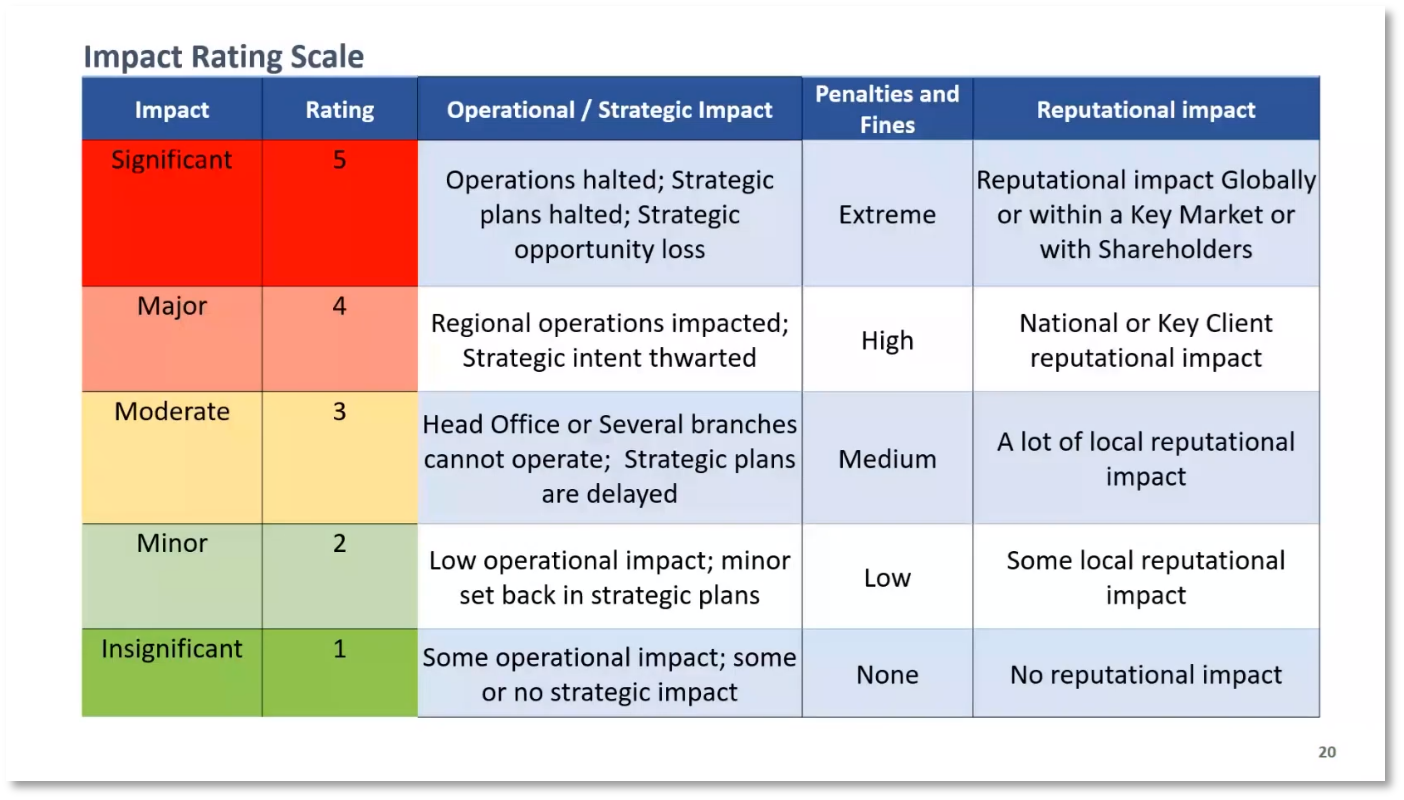
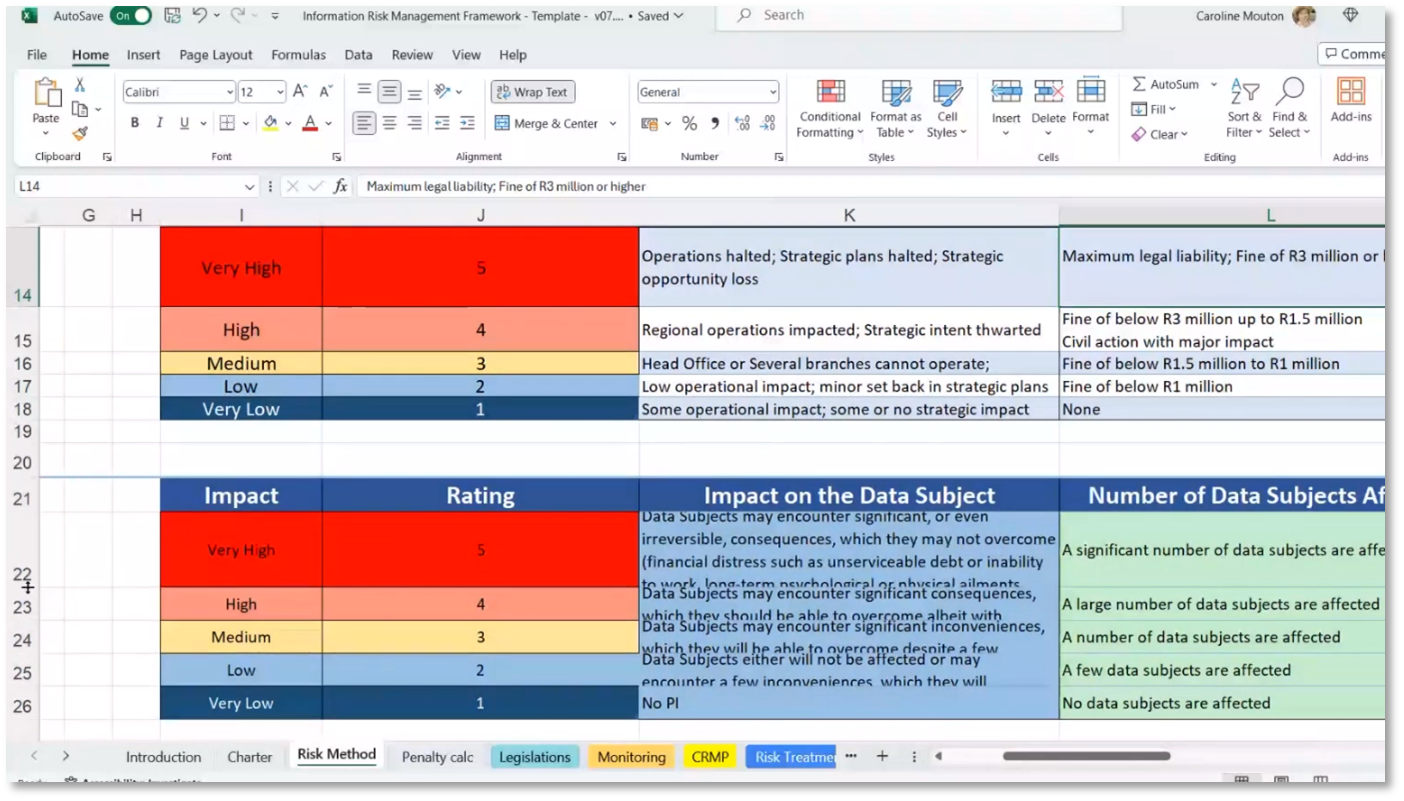
To comply with General Data Protection Regulation (GDPR), businesses must maintain a register of all business processes known as The ROPA. This tool is designed to help businesses understand their privacy obligations and requirements by outlining all obligations and assisting in understanding what they entail. The ROPA uses a rating scale to assess the impact and likelihood of risks, with risk assessment involving consideration of both the impact on individuals and the organisation. It is important to note that personal perceptions of risk may differ from the organisational perception of risk.
Figure 13 Impact Rating Scale
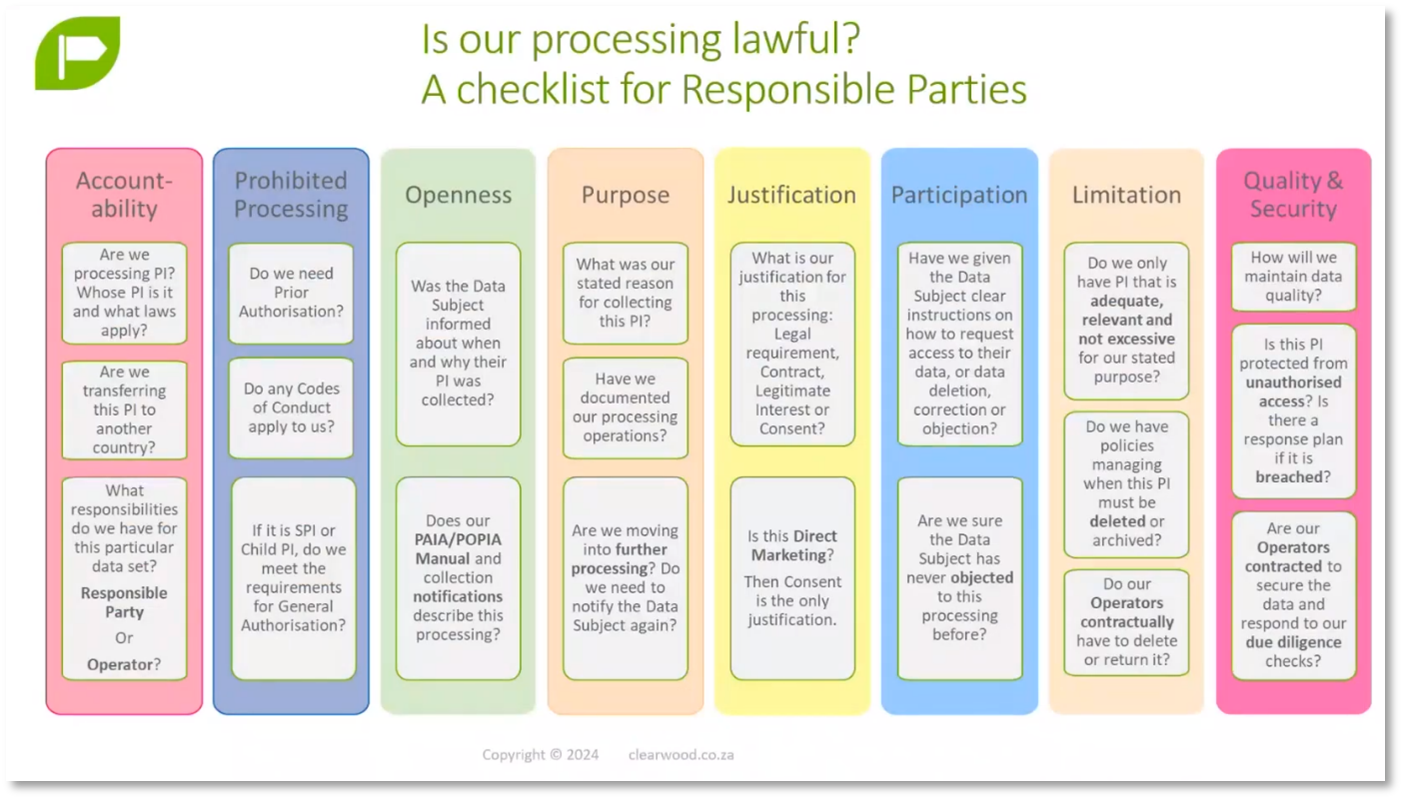
Personal Information Impact Assessment and Penalties in POPIA
The Personal Information Impact Assessment (PIIA) is a process that examines the operational and strategic impact, openness, justification, and participation in processing personal information. It considers the data subject's perspective to ensure compliance with requirements for accountability and transparency in data processing. The Protection of Personal Information Act (POPIA) in South Africa imposes penalties for non-compliance, including a 10 million Rand fine, a 1 million Rand fine, and civil liability for allowing complaints and lawsuits against an organisation. The penalties cover unauthorised use of financial account numbers, activities requiring prior authorisation, and actions that may lead to complaints to the regulator. Practical examples of PIIA and POPIA penalties can be demonstrated using spreadsheets and an information risk management framework.
Figure 14 Checklist for Responsible parties
Figure 15 Riskiest Risks Approach
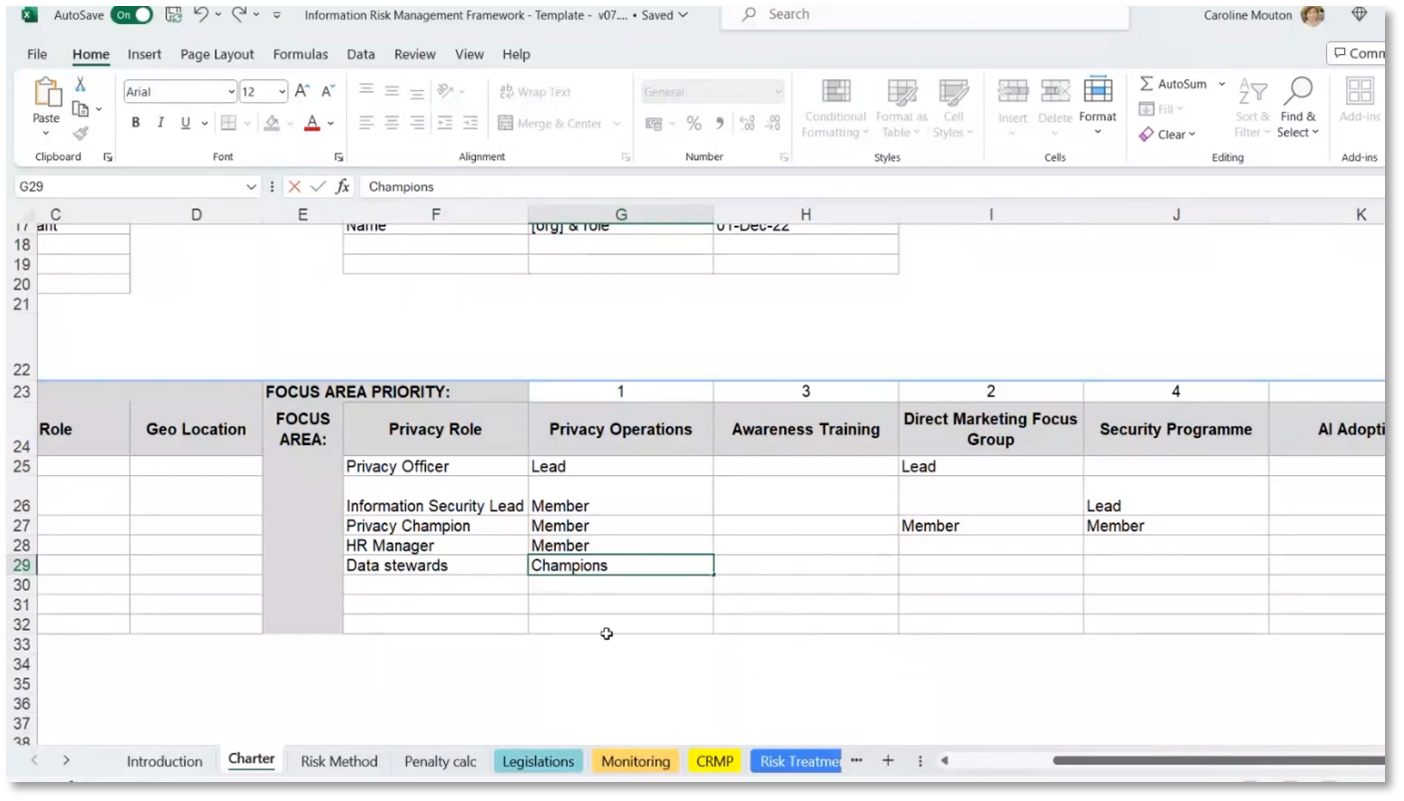
Privacy and Security Program for 2024
The organisation has a comprehensive privacy compliance framework addresses risk management, legislative monitoring, and personal information impact assessments. The framework integrates ISO and DAMA standards and applies different standards, including DM. The privacy and security program for 2024 outlines outcomes, scope in terms of legislation, and compliance requirements for South African privacy obligations and security management. The program includes participants from different companies, third parties, outsourced service providers, and strategic partners with specific roles in the program, such as the privacy officer, information security personnel, HR manager, and data stewards.
Figure 16 Information Risk Management Framework
Figure 17 Information Risk Management Framework continued
Figure 18 Information Risk Management Framework continued
Privacy and Security Program Planning
Caroline covers various aspects of combining security and privacy in awareness training, such as direct marketing ownership by the privacy officer and marketing manager, membership in the security program for privacy champions, data stewards, and HR managers, integration of AI and GPT functionality in the information risk program, importance of privacy monitoring and management, comparison of privacy program planning to a RACI model, and consideration of focus groups, Centre of Excellence, and communities of practice for direct marketing management.
Risk Management and Compliance
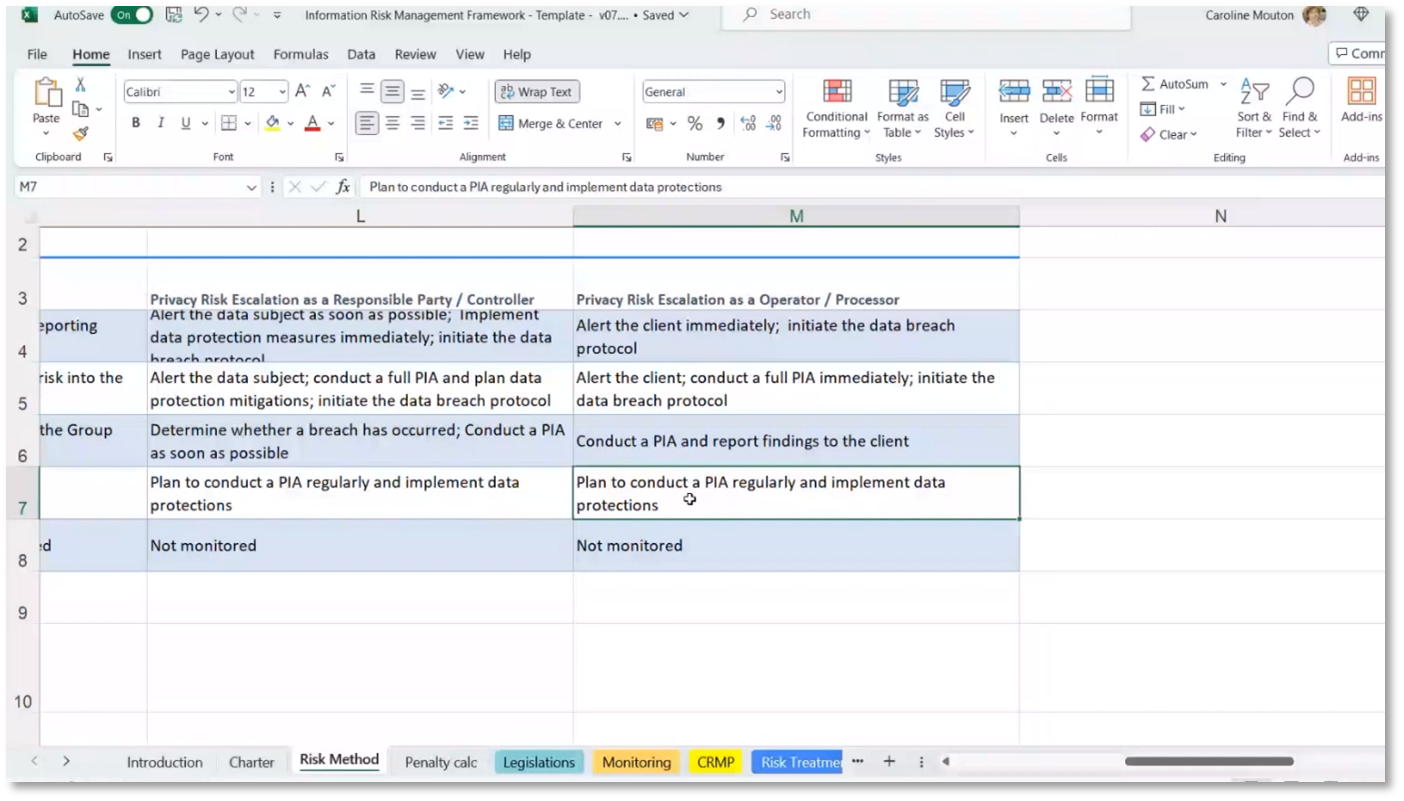
Direct marketing is carried out by the sales and marketing teams while complying with the Protection of Personal Information Act (POPIA). Establishing a community of practice or focus group is important to ensure compliance. Risk management involves evaluating the probability and impact of breaches, similar to IT service management. Probability is rated from not applicable to almost certain, and impact ranges from low to extremely high. The organisation should determine what constitutes high and moderate risks and how to escalate them. High-impact privacy risks should trigger the data breach protocol and alert everyone.
Figure 19 Information Risk Management Framework continued
Privacy Impact Assessment and Its Importance
Caroline shares that a privacy impact assessment is crucial for companies to understand how personal information is accessed and used. Its purpose is to mitigate risks and determine the potential impact on the company and data subjects. A company's approach to risk management varies depending on its perception of what constitutes a high impact. Privacy impact assessments also consider the potential consequences for data subjects, such as using biometric equipment in sensitive areas like banking. This assessment helps evaluate the risks and implications of using technologies like face recognition systems.
Figure 20 Information Risk Management Framework continued
Figure 21 Information Risk Management Framework continued
Privacy Impact Assessment and Data Protection Legislation
Data privacy and protection are crucial for individuals and businesses, and the privacy impact assessment process evaluates potential risks and impacts of data breaches. This process considers key metrics like the number of people affected, the type of personal information involved, and the types of processing. Certain types of processing may require prior authorisation, and compliance information officers play a crucial role in overseeing the process and ensuring necessary measures are taken to protect data. Having a risk register and mitigation processes is important for managing and mitigating risks effectively, reflecting a mature compliance management function.
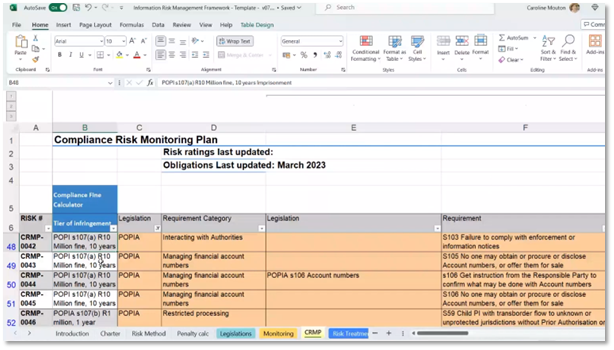
Compliance Risk Monitoring Plan
The Compliance Risk Monitoring Plan is designed to ensure that the company manages financial account numbers per the law and to mitigate inherent risks. It includes assessing the company's risk level, identifying specific risks and obligations, and proposing a risk treatment plan (RTP) to secure financial account numbers. The risk level is found to be moderate due to the unlikelihood of non-compliance. The plan suggests simplifying the compliance risk management approach to effectively monitor the riskiest risks, including privacy legislation and payroll management obligations. Moreover, it includes a list of obligations, such as maximum legal and civil liability, to assess compliance and assign responsibility for mitigating specific risks.
Figure 22 Compliance Risk Monitoring Plan
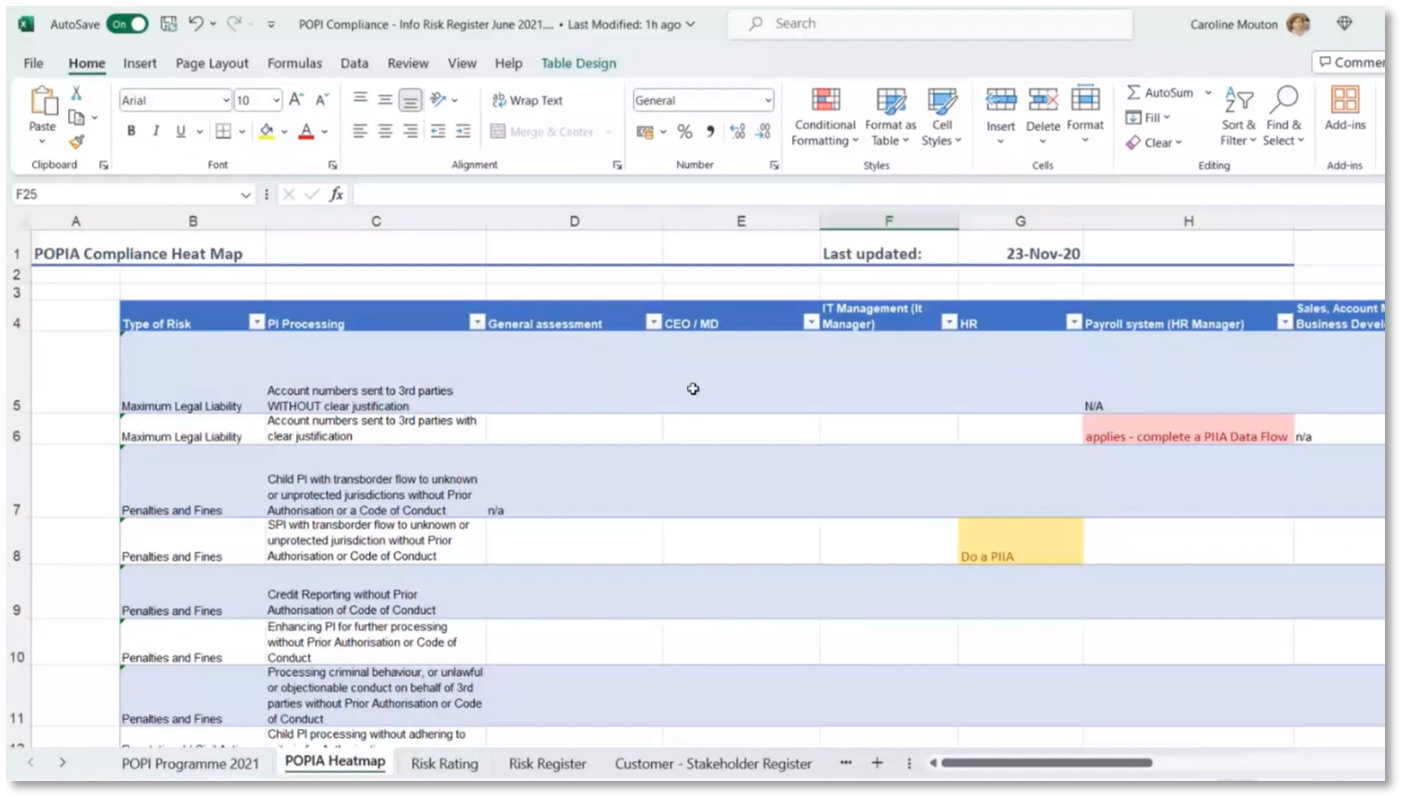
Figure 23 POPIA Compliance Heat Map
Risk Assessment in the Payroll System
Caroline notes that it's essential to assess the security safeguards for the payroll system to ensure its security. If automated decision-making is used, a privacy impact assessment is necessary. Additionally, processing information about children without pROPA authorisation requires the same. Identifying and prioritising the most critical risks is necessary to address them first. A simplified risk assessment tool can help to assess the departments, teams, systems, and business processes against specific obligations. The process can be used to identify and address potential risks and compliance issues within the payroll system.
If you want to receive the recording, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!