Using PI – Being Purposeful in How You Use PI
Executive Summary
Introduction to Data Flow Diagrams and their Importance in Privacy Discussions. Industry Roles and Specializations. How to Approach Software Functionality and Technical Architecture in Business. Data Flow Diagram - Customer Onboarding Process. Creating a Website Registration Process. Workflow and Data Transfer Process. Process of accessing data from Refinitiv for KYC background checks. Challenges in Customer Registration and Data Collection Process. Workflow, Escalation, and Decision-Making Processes. Clarifying Data Flow and Privacy Policy. Data Flow Diagram and Cross-Border Transfer in Caroline's CRM System. Discussion on data processing and cross-border transfers. Managing sensitive information in Salesforce. Privacy Concerns in Data Handling and Customer Access to Financial Services. Automated Decision Making and the Need for Manual Review. Automated Decision Making and Data Hosting Risks. Prior Authorization for Sending Special Personal Information. Conversations on Compliance and Data Retention.
Webinar Details
Webinar Title: USING PI – BEING PURPOSEFUL IN HOW YOU USE PI
Webinar Date: 22nd June 2023
Webinar Presenter: Caroline Mouton
Meetup Group: Data Privacy & Protection with Caroline Mouton
Write-up Author: Caroline Mouton
Contents
Executive Summary
Webinar Details
Introduction to Data Flow Diagrams and their Importance in Privacy Discussions
Industry Roles and Specializations
How to Approach Software Functionality and Technical Architecture in Business
Data Flow Diagram - Customer Onboarding Process
Creating a Website Registration Process
Workflow and Data Transfer Process
Process of accessing data from Refinitiv for KYC background checks
Challenges in Customer Registration and Data Collection Process
Workflow, Escalation, and Decision-Making Process
Clarifying Data Flow and Privacy Policy
Data Flow Diagram and Cross-Border Transfer in Caroline's CRM System
Discussion on data processing and cross-border transfers
Legal Obligations and Exemptions for Personal Information
Managing sensitive information in Salesforce
Privacy Concerns in Data Handling and Customer Access to Financial Services
Automated Decision-Making and the Need for Manual Review
Automated Decision-Making and Data Hosting Risks
Prior Authorization for Sending Special Personal Information
Conversations on Compliance and Data Retention
Introduction to Data Flow Diagrams and their Importance in Privacy Discussions
Howard Diesel suggests delving into data flow diagrams for privacy concerns. Caroline proposes evaluating the necessity of data flow diagrams versus other approaches. She plans to introduce data flows and their role in making sense of information, emphasising visuals’ importance in facilitating data protection and accountability discussions. Participants are encouraged to share their roles and understanding of data flow diagrams for further discussions.
Industry Roles and Specializations
Ross Diesel is interested in engine development and has experience in advisory, consulting, and data governance. Van Rensburg, Maliska is confirmed to work in the consulting industry, specifically in financial services, with a wide range of rules. Howard Diesel discusses risk data aggregation and BCBS 239. Jane Makgeledisa is a data steward in banking. Tuyakula Musheko works as a data analyst in the media industry. Rizwana Cassim is a financial services data architect. Caroline focuses on data flow in the finance industry.
How to Approach Software Functionality and Technical Architecture in Business
Caroline explains how she collaborates with business analysts and developers to understand application functionality and technical specifications. She stresses the importance of considering host platforms, API integration, and cross-platform presentation aspects. Caroline emphasises the need to make information relatable to different disciplines and professions, citing an example of data flow in a bank's mainframe system. She recommends using visualisation tools like Visio, draw IO, or diagrams.net to aid in explaining concepts and suggests utilising the customer onboarding process as an example.
Figure 1 Demonstration of using Viso to aid explanations
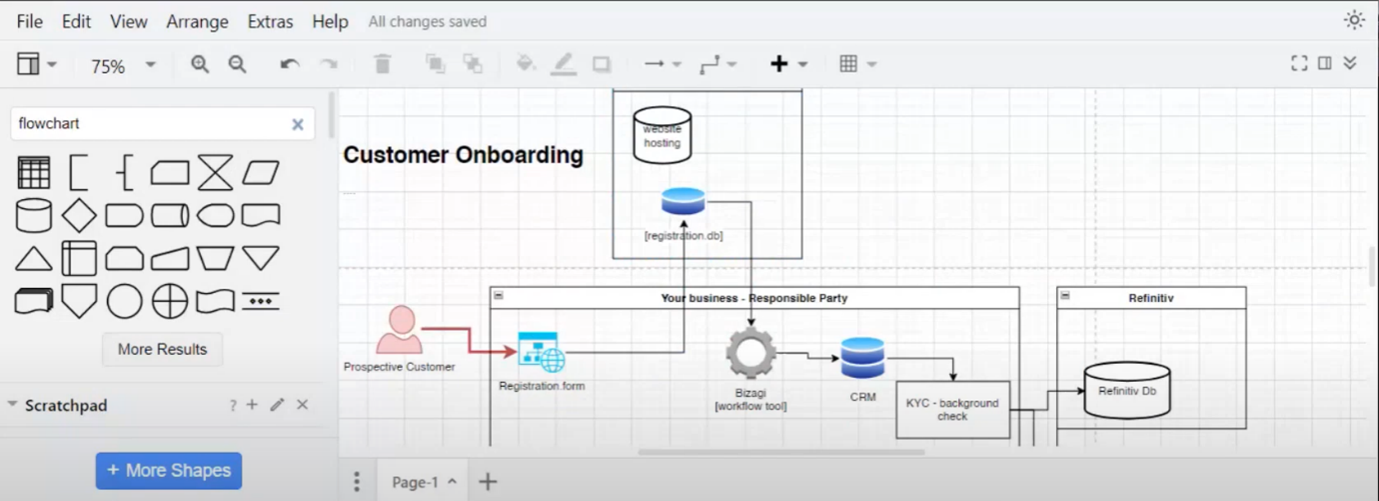
Data Flow Diagram - Customer Onboarding Process
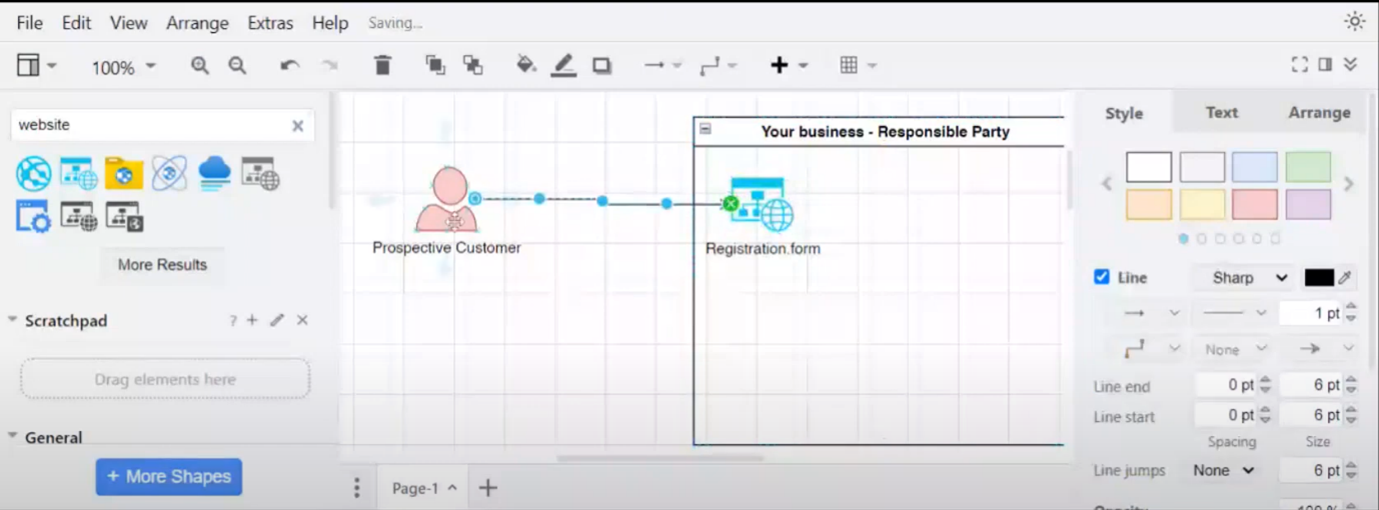
The discussion begins with the importance of being data-centric and data-subject-centric, specifically in onboarding a prospective customer. The data flow diagram focuses on the customer onboarding process and using an online application form. An authorisation boundary is established, with the legal entity taking responsibility. Finally, whether the onboarding process is self-directed or prompted by a marketing campaign is addressed.
Figure 2 Data Flow Diagram - Customer Onboarding Process
Creating a Website Registration Process
The website page to direct customers is named the business homepage. The registration form is explained for inputting personal information into a database, which may feed into a workflow tool for customer onboarding. The purpose is to clarify the customer onboarding process.
Figure 3 Creating a Website Registration Process
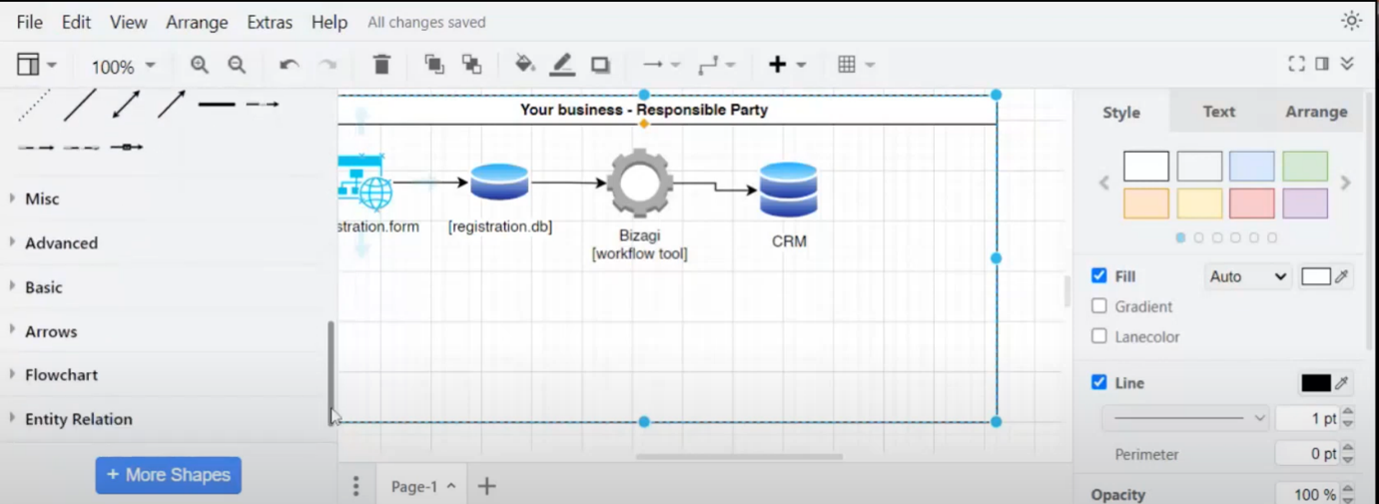
Workflow and Data Transfer Process
Caroline explains the process of registration, including the use of tools like Bizagi, World Check or KYC, and a workflow tool that transfers data into a CRM system. She emphasises the importance of determining the minimum amount of critical data required for the process.
Figure 4 Workflow and Data Transfer Process
Process of accessing data from Refinitiv for KYC background checks
The group discusses accessing data from Refinitiv for KYC background checks. There is confusion about "wolf pick" and its relation to the database. Refinitiv is clarified as a separate database for checking. The KYC process and transferring data from Refinitiv to their system are discussed. Methods of accessing Refinitiv, such as using an API or manual login, are mentioned. Howard asks Ross about their check process.
Figure 5 Process of accessing data from Refinitiv for KYC background checks
Challenges in Customer Registration and Data Collection Process
The customer registration process involves collecting all customer details during the sale and transferring them to the company. Home Affairs may experience downtime, causing delays in immediate customer engagement. Online registration has potential issues, which can lead to unreliable automated flows. Queue build-up and registration delays can affect big retailers' efficiency. Unstructured data flows can occur, leading to unconventional methods like photographing ID documents with cell phones. Teller errors, such as entering their phone numbers instead of customer data, can result in inaccurate information.
Figure 6 Challenges in Customer Registration and Data Collection Process
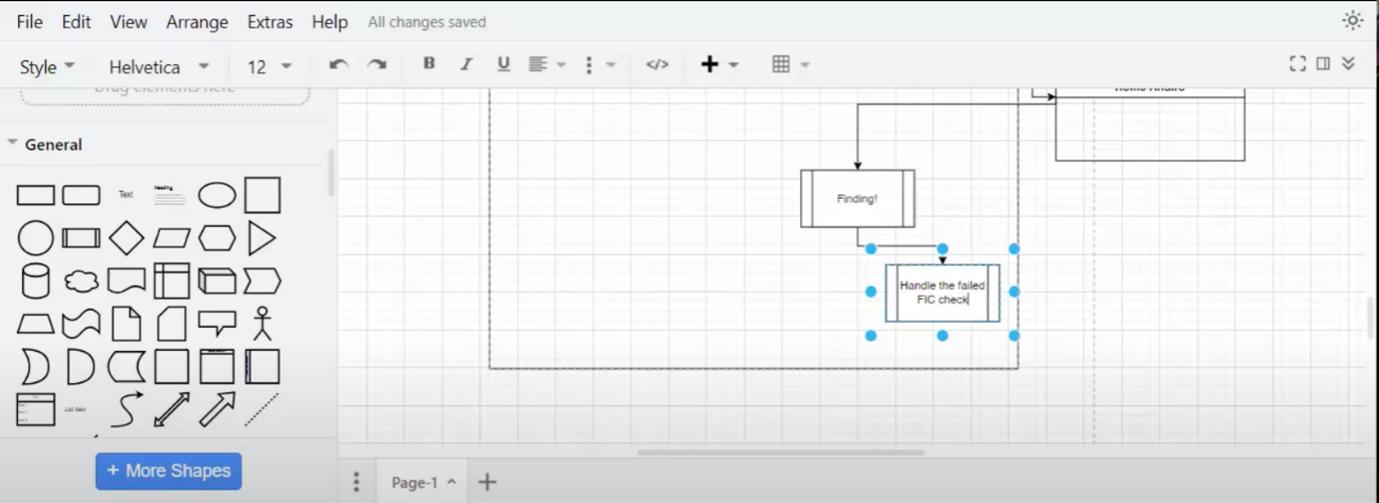
Workflow, Escalation, and Decision-Making Process
The process starts with filling in a form on the website. The data is transferred to the CRM system, which initiates a KYC background check. If a person fails the inspection, the team handles and escalates the issue, involving Standard Bank if necessary. Conversations with Home Affairs are necessary to grant customers grace. Caroline focuses on when the process works correctly.
Figure 7 Workflow, Escalation, and Decision-Making Process
Clarifying Data Flow and Privacy Policy
Ross Diesel and Caroline discuss handling functions, fixing checks, data flow, and identifying data subjects. They question storing pictures and emphasise using user profiles. The registration form may be hosted on a third-party service like Hetzner, and data flows to the database via the hosting service. Salesforce may serve as the CRM.
Figure 8 Clarifying Data Flow and Privacy Policy
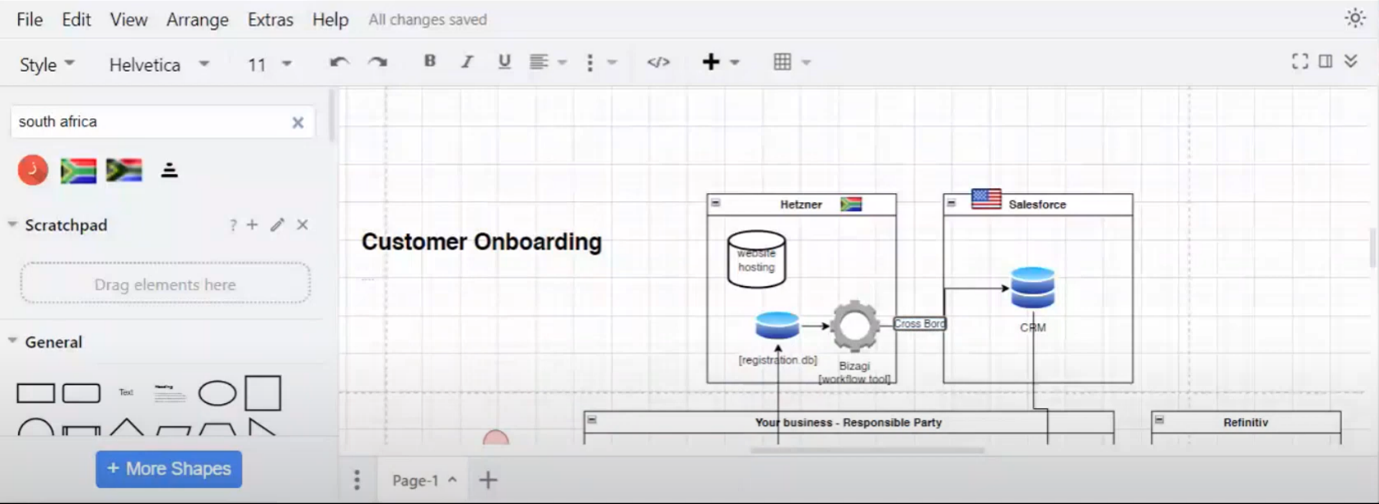
Data Flow Diagram and Cross-Border Transfer in Caroline's CRM System
Caroline explains that in her CRM system, operators process personal information like supplies. She and Howard discuss hosting the data, defaulting to the USA, but Caroline clarifies that it is hosted in South Africa using a flag. Howard corrects Caroline, stating that the flag represents Saudi Arabia. Caroline emphasises data protection and encryption and mentions backup servers. She discusses the involvement of Hits Night in processing the data and highlights the need for privacy policy transparency regarding data sharing with service providers. Caroline explains that the CRM system is currently in America but planning to move to the EU, referencing this as a cross-border transfer in the data flow diagram.
Figure 9 Data Flow Diagram and Cross-Border Transfer in Caroline's CRM System
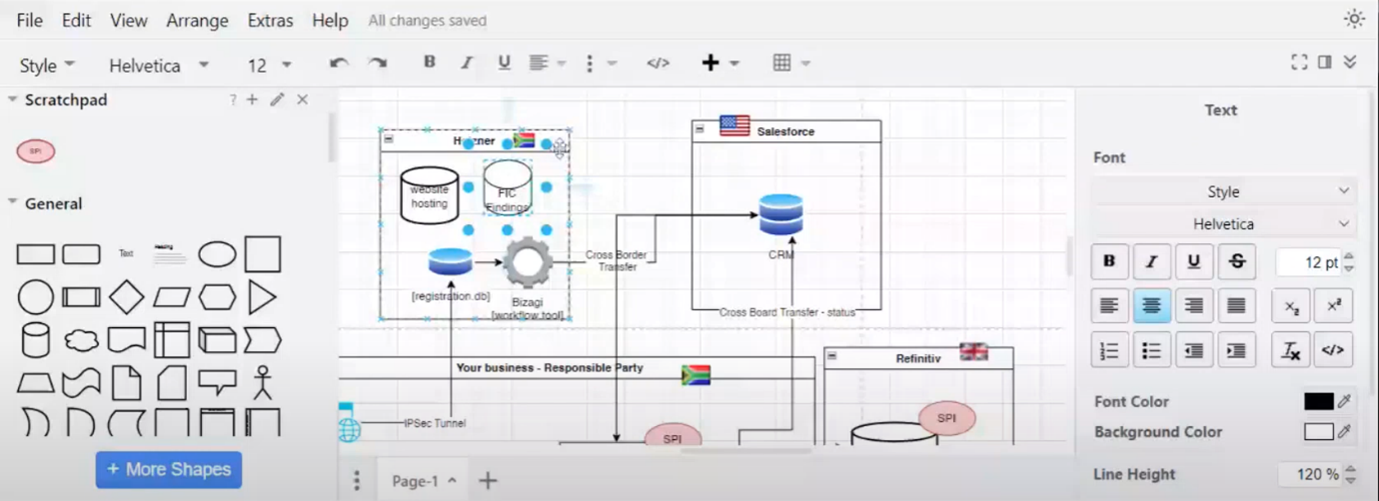
Discussion on data processing and cross-border transfers
Caroline discusses finding information, Refinitiv's colour coding system, data types, information control, London location, jurisdiction, capturing findings in CRM, cross-border transfers, and blacklisting.
Figure 10 Discussion on data processing and cross-border transfers
Legal Obligations and Exemptions for Personal Information
Howard and Caroline discuss reasons for blacklisting individuals, including legal and terrorist issues. Caroline confirms that Refinitiv keeps all blacklisting data, prompting Howard's inquiry about the legal basis for inputting personal information. Caroline explains that background checks are legally required, citing Fika's requirement. The group debates whether to inform data subjects about suspicions of terrorist activity, with Caroline citing an exemption under the Protection of Personal Information Act (POPI). Howard adds that national security and freedom of information are valid reasons for not disclosing specific data. Caroline suggests a way to indicate non-disclosure of specific findings in the CRM while still fulfilling disclosure requirements for other data.
Figure 11 Legal Obligations and Exemptions for Personal Information
Managing sensitive information in Salesforce
To ensure the secure handling of sensitive information, restrict access and implement a system for managing criminal or objectionable behaviour. Store rejection results and block rejected customers from further transfers.
Figure 12 Managing sensitive information in Salesforce
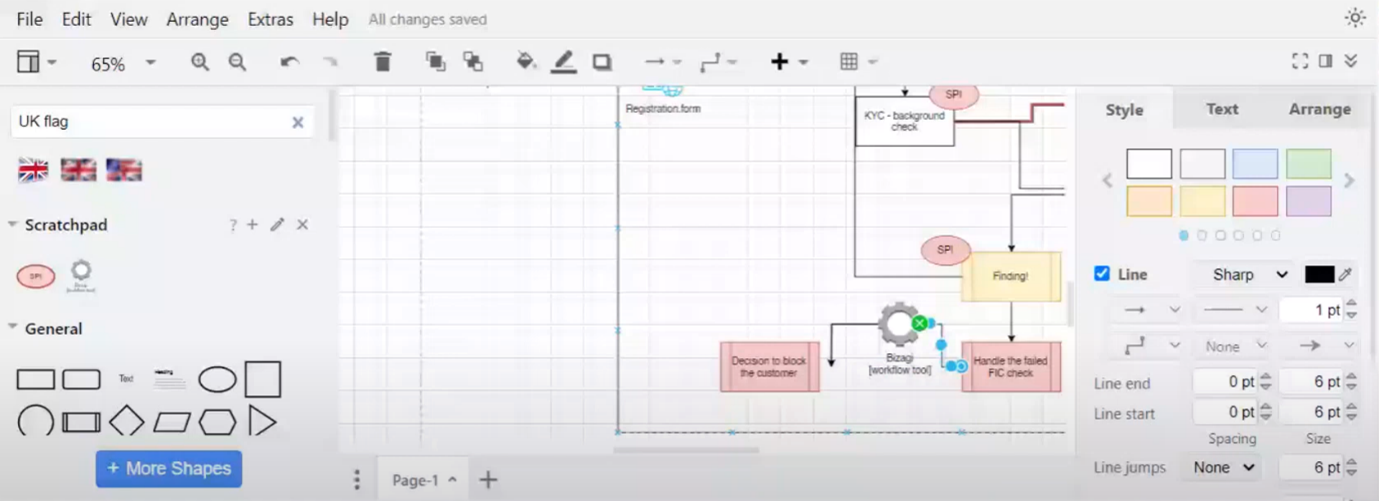
Privacy Concerns in Data Handling and Customer Access to Financial Services
Ross clarifies that his company processed customer data for Standard Bank and the retailer but did not own the customer. Responsibility for customer data lies with the bank. Standard Bank would handle suspects, and Diesel's company would only handle minimal customer information. Caroline raises a question about the decision to block the customer and its potential effect on accessing financial services. The privacy concern is that such a decision could prevent the data subject from accessing financial services. Caroline emphasises the importance of considering the tools used in making such decisions, particularly if the decision is purely automated.
Figure 13 Privacy Concerns in Data Handling and Customer Access to Financial Services
Automated Decision-Making and the Need for Manual Review
Howard, Caroline, and Ross discuss the importance of manual checks in the automated decision-making process. They acknowledge the seriousness of the volume of incidents and the need for a review process to investigate rejected cases. Howard expresses concerns about replicating manual decision-making with AI tools.
Figure 14 Automated Decision-Making and the Need for Manual Review
Automated Decision Making and Data Hosting Risks
Caroline stresses the importance of avoiding the negative consequences of automated decision-making. She recommends delaying decisions for verification and questioning who checks and verifies these decisions. Caroline also highlights the need to understand data hosting contracts and the location of data, including the data processor's location. Lastly, she mentions the risks of transferring objectionable behaviour or information, such as personal information or information about minors.
Prior Authorization for Sending Special Personal Information
Caroline recommends exploring prior authorisation when sending personal information to a country without adequate data protection, such as the US. Prior authorisation is defined as a process related to processing personal information on behalf of a third party or transferring personal information to a foreign country without adequate protection. Four situations where prior authorisation is required are outlined, and it is suggested that organisations establish a policy or guideline on privacy for compliance officers and business analysts.
Figure 15 Prior Authorization for Sending Special Personal Information
Conversations on Compliance and Data Retention
Technical teams should consult compliance for adherence to policies and regulations. Authorisation is not required. Visual aids simplify conversations. Consider data capture and retention policies for temporary databases.
If you want to receive the recording, kindly contact Debbie (social@modelwaresystems.com)
Don’t forget to join our exciting LinkedIn and Meetup data communities not to miss out!