Data Privacy & Unstructured Data - DAMA SA
Executive Summary:
Caroline Mouton covers various aspects of information management, privacy compliance, and data security.
She includes the importance of document and records management and the differences between documents and records.
She explained the challenges of managing records and metadata, the relationship between technology and information, enterprise information management, and records management.
She reviews the significance of website snapshots as records, privacy risks, data breaches, unstructured data risks, and sharing and securing access to team spaces and channels.
Additionally, Caroline sheds light on tools for mapping data flow and creating diagrams, data flow and risk assessment in website form process, data storage and management, the importance of structured data and data visualisation in business, the importance of language and data management in the workplace, the importance of data governance and tools in content management, the importance of case management and workflow tools in business operations, and importance of data management and tools for incident management and compliance.
Lastly, Caroline provides a quick playbook for file shares and managing privacy risks with data flow diagrams, effective communication, and simplified diagrams.
Webinar Details:
Title: Data Privacy & Unstructured Data - DAMA SA
Date: 10 May 2022
Presenter: Caroline Mouton
Meetup Group: Data Privacy & Protection with Caroline Mouton
Write-up Author: Howard Diesel
Contents
Understanding the Practical Implications of Privacy and Property Compliance.
The Importance of Document and Records Management
Differences Between Documents and Records.
Importance and Challenges of Managing Records and Metadata.
Understanding the Relationship Between Technology and Information.
Enterprise Information Management (EIM) and Records Management
Importance of Website Snapshots as Records.
Notes on Privacy Risk and Responsibility in Publishing.
Data Breaches and Unstructured Data Risks: Lessons Learned.
Sharing and Securing Access to Team Spaces and Channels.
Tools for Mapping Data Flow and Creating Diagrams.
Data Flow and Risk Assessment in Website Form Process.
Understanding Data Storage and Management
Importance of Structured Data and Data Visualization in Business.
Importance of Language and Data Management in the Workplace.
Importance of Data Governance and Tools in Content Management
Importance of Case Management and Workflow Tools in Business Operations.
Importance of Data Management and Tools for Incident Management and Compliance.
Quick playbook for file shares.
Managing Privacy Risks with Data Flow Diagrams.
Effective Communication and Simplified Diagrams.
Tips for Communicating Complex Concepts.
Understanding the Practical Implications of Data Privacy and Protection Compliance
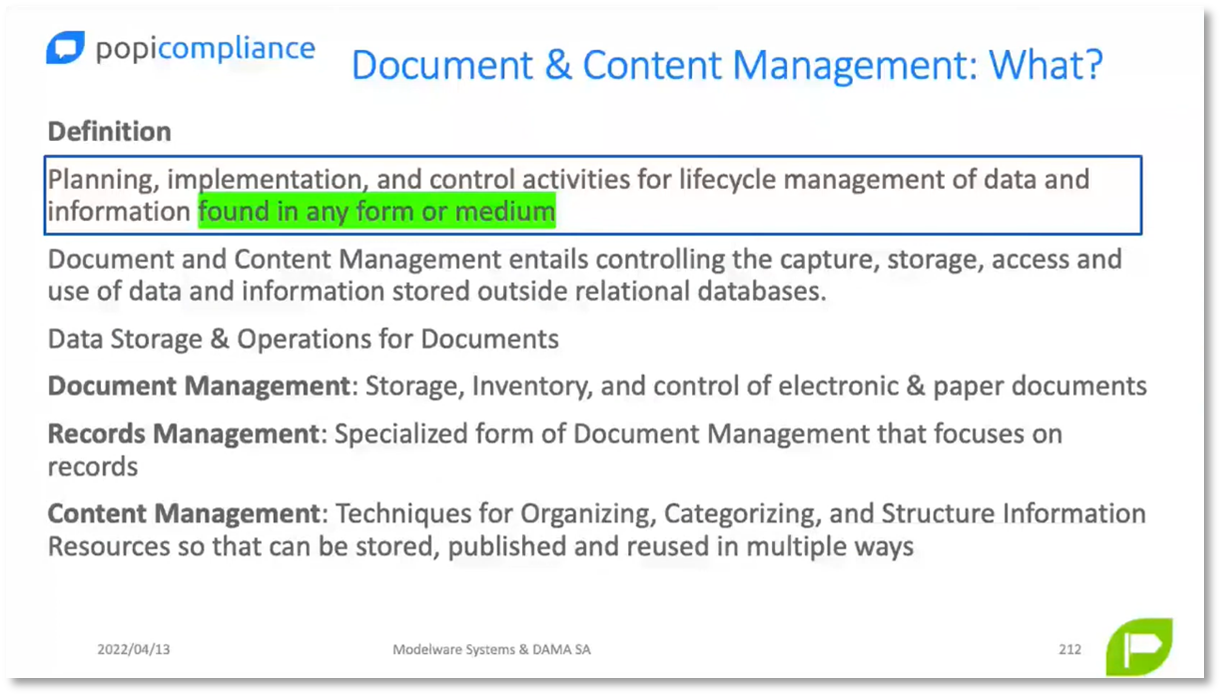
The practical implications and management of privacy and protection are covered. The discussion includes an overview of document and content management, emphasising the data management lifecycle, including creation, storage, sharing, consultation, and deletion. Unstructured data presents challenges in document management within the context of the e Wheel, and Caroline offers perspectives from enterprise content management and information governance. While she acknowledges a background in information governance and management, seeking legal advice is encouraged for understanding risks and penalties related to copy of privacy. The webinar provides valuable insights for organisations to manage their data per privacy and property compliance laws.
Figure 1 About me: Caroline Mouton
The Importance of Document and Records Management
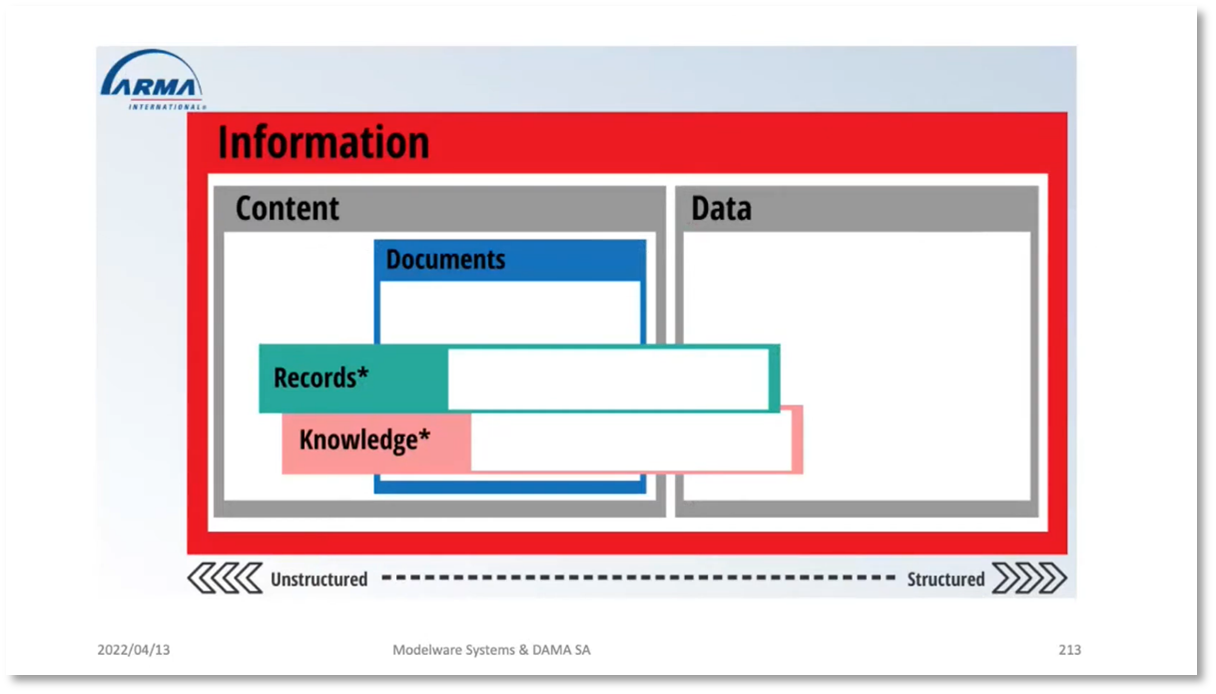
Content is a term that encompasses various formats, such as documents, spreadsheets, and records. Filing systems and file plans are crucial to make it easier to locate stored content. In the healthcare industry, patient files are typically stored in a logical sequence, such as by surname, with unique reference numbers. However, with the advent of personal computers, structured records management practices have been disregarded. To ensure structured storage, publishing, backup, and content management, it is essential to follow the principles of document management, records management, and content management. Information includes structured data and content, with documents as a subset of content and records as a subset of documents. Collaboration on a document may involve multiple iterations before a finalised PDF version is created.
Figure 2 The Importance of Document and Records Management
Figure 3 The Importance of Document and Records Management Continued
Differences Between Documents and Records
Documents and records are two distinct types of information. Documents are dynamic and can change over time, with audit trails, change histories, and varying access levels. On the other hand, records capture a specific event or occurrence and serve as evidence. Contracts are an example of records.
In the medical field, litmus tests are considered records and are commonly included in patient files, especially in hospitals. Understanding the difference between documents and records is important to ensure proper handling and management of sensitive information.
Importance and Challenges of Managing Records and Metadata
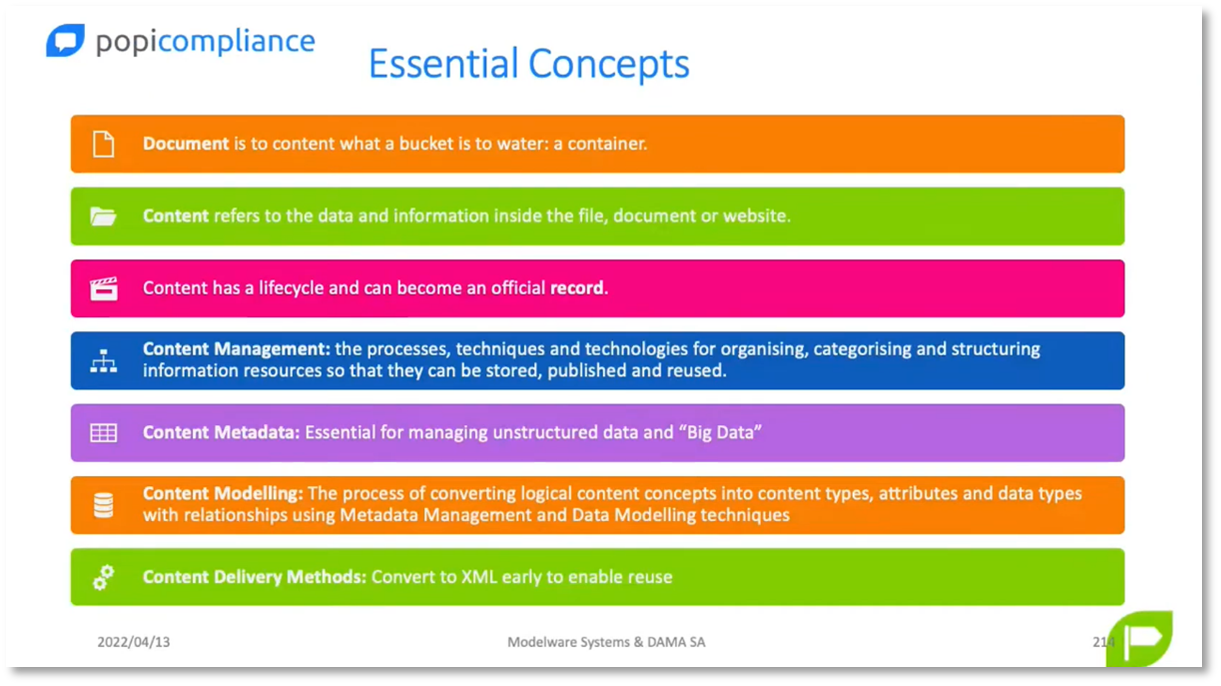
Proper sanitation and equipment testing are essential in healthcare settings to prevent contamination. Litmus tests are used to determine the cleanliness of equipment, and the results are stored as part of a patient's record. However, storing records can be challenging, especially involving physical items such as CCTV footage. CCTV footage is preserved as evidence in cases of theft or incidents. Managing records involves organising data, emails, documents, and communication in a structured manner. This is where content management comes in, including metadata creation and tagging, to make information discoverable and searchable. Hashtags on Twitter and metadata in SharePoint are similar tools that make content more findable. Folder structures may not always be efficient, so tags and metadata can be used to locate documents more easily.
Figure 4 Essential Concepts
Understanding the Relationship Between Technology and Information
Personal information must be managed effectively to ensure privacy. King 4 is the recommended guide for directors. Information refers to data, records, and knowledge that comprise an organisation's intellectual capital, while technology encompasses the infrastructure, systems, devices, and software that carry the information. The business owner should specify the desired outcomes, with data, information, and document owners responsible for their management. Information governance involves managing IT infrastructure, information systems, information security, enterprise content, and data. Managing information governance across all aspects of the organisation is crucial to ensure privacy.
Figure 5 Information Governance
Figure 6 What we need to manage right now
Enterprise Information Management (EIM) and Records Management
Enterprise Information Management (EIM) is an umbrella term that encompasses structured data (such as master data databases), semi-structured data (like XML), and unstructured content management. The latter includes documents, websites, and records. Records serve as evidence of transactions and content at a specific time. To ensure privacy, consent records should be tracked, including the message shown, the date and time of consent, and the date and time of withdrawal. An audit trail is necessary to demonstrate to regulators the content, dates, and times associated with consent. It is important to note that publishing content on a website does not automatically make it a record since websites are subject to change.
Figure 7 Layers of Information Governance
Figure 8 What is Information?
Importance of Website Snapshots as Records
To ensure a website can act as an accurate record, it must be possible to recreate it from a specific point in time. This requires the company managing the website to keep track of versions of all pages and treat them as records. Overwriting website content without preserving previous versions can eliminate the record of what customers have consented to. The distinction between a document and a record depends on how the web page is stored. A website snapshot at a specific date and time can serve as a record, while the published content can still be changed.
Notes on Privacy Risk and Responsibility in Publishing
Caroline covers key points related to privacy and information governance. She includes the burden of proof falling on the responsible party in case of non-adherence to consent agreements, the definition of a web page as a record, the insufficiency of screenshots as records, and the significance of backing up a web page or website at a specific time. Additionally, Caroline highlights the need for additional measures beyond publishing to serve as a record, the role of enterprise content management in mitigating privacy risks, and the risk of accidental sharing of documents, contributing to 40% of breaches. Furthermore, she points out the significant risk of inadequate control over document sharing, such as not revoking access after an employee leaves.
Figure 9 Layers of Information Governance pt.2
Data Breaches and Unstructured Data Risks: Lessons Learned
The Experian data breach of a few years ago served as a wake-up call for companies to implement security protocols and checks to prevent unauthorised access to data. Third-party data breaches are a growing concern due to the ease of sharing unstructured and unmanaged documents, which can create multiple copies and a potential loss of control.
It is crucial to carefully consider what data should be allowed to become unstructured to avoid losing control and creating an exponential number of copies. Shockingly, only 5% of company folders are properly protected, which suggests a lack of understanding or implementation of access management.
Moving folders or changing access controls can inadvertently break hierarchies and expose sensitive information, as observed in some organisations using Windows and file shares. Therefore, it is essential to understand the access controls and features of collaboration tools such as Google Workspace and Microsoft Teams to prevent inadvertent sharing or external access.
Figure 10 The risks
Sharing and Securing Access to Team Spaces and Channels
The challenges and potential risks associated with sharing access within teams are emphasised, and careful consideration and understanding of the technologies involved are needed. The webinar also mentions the importance of balancing security and functionality and the potential for people to find ways around the security measures. Furthermore, it touches on the issue of delay in productivity caused by a business unit not completing onboarding processes on time. As a workaround, some people send attachments via email instead of securely sharing them in teams.
Tools for Mapping Data Flow and Creating Diagrams
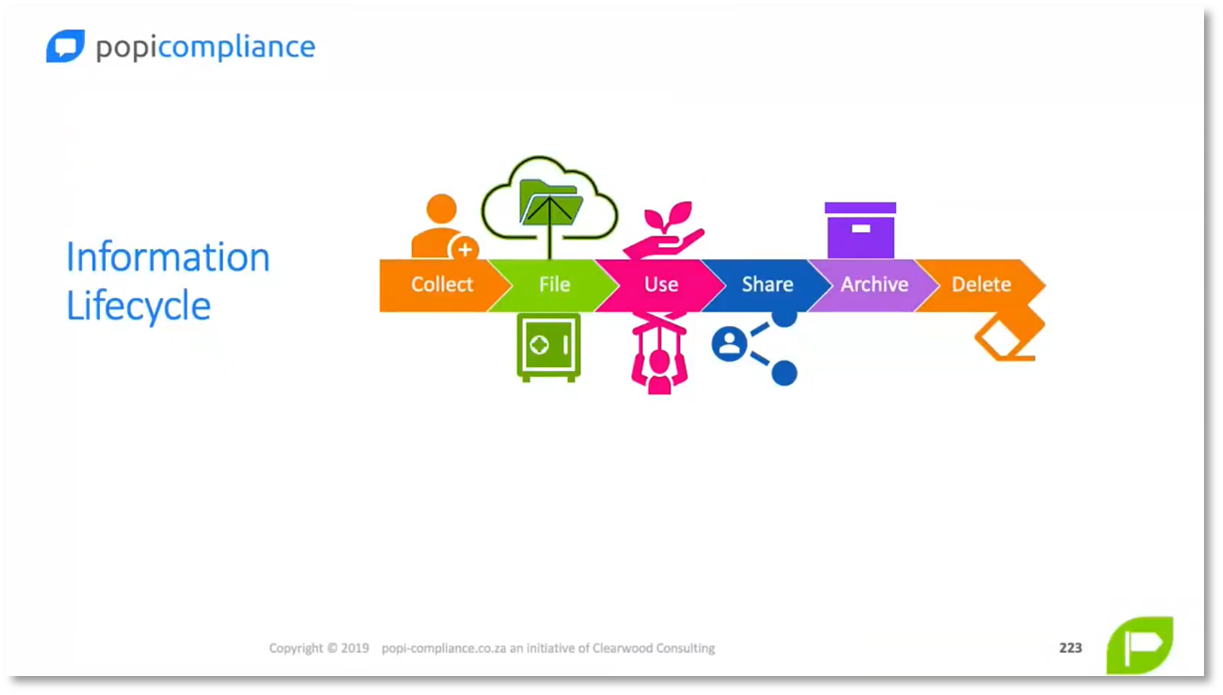
Caroline highlights the importance of use cases and understanding information flow for effective communication and productivity. She emphasises that security measures should enable the fulfilment of the information lifecycle rather than impede productivity. Caroline recommends using tools like Visio, online tools, or simple flowchart diagramming tools for mapping data flow and placing safeguards. She also suggests starting with the riskiest risks and then expanding when creating data flow diagrams, essentially workflows that can be as complex or simple as needed. Lastly, Caroline recommends using Draw.io, a convenient tool for creating and saving diagrams locally.
Figure 11 Information Lifecycle
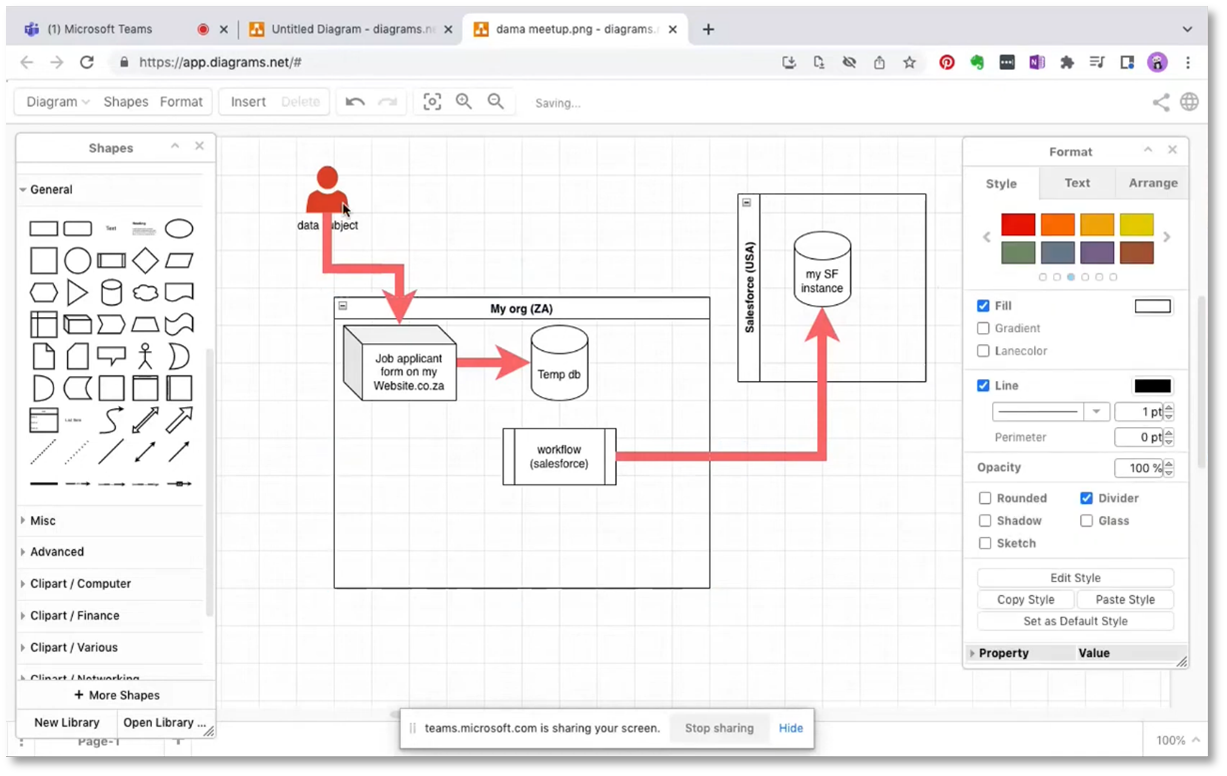
Data Flow and Risk Assessment in Website Form Process
Caroline creates a container that uses an orange colour to organise data subjects' information, with the specific example of a job applicant form on their website. The form sends the data to a temporary database, which flows into a workflow tool (likely Salesforce). Caroline notes that as a third-party provider, Salesforce hosts the data in South Africa while the organisation is in the USA. She also identifies a potential risk with the temporary database and marks it as red with an attached task for removal. Caroline highlights the importance of efficient data management and the potential risks involved.
Figure 12 Data Flow and Risk Assessment in Website Form Process
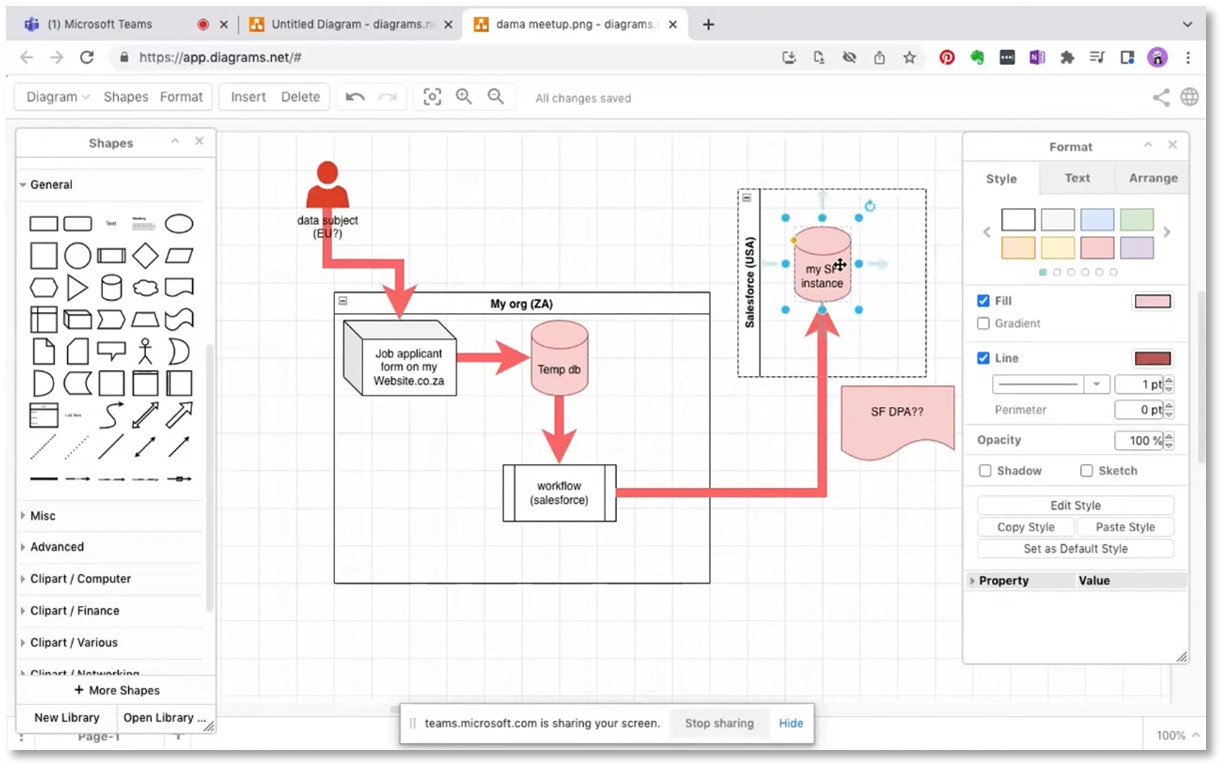
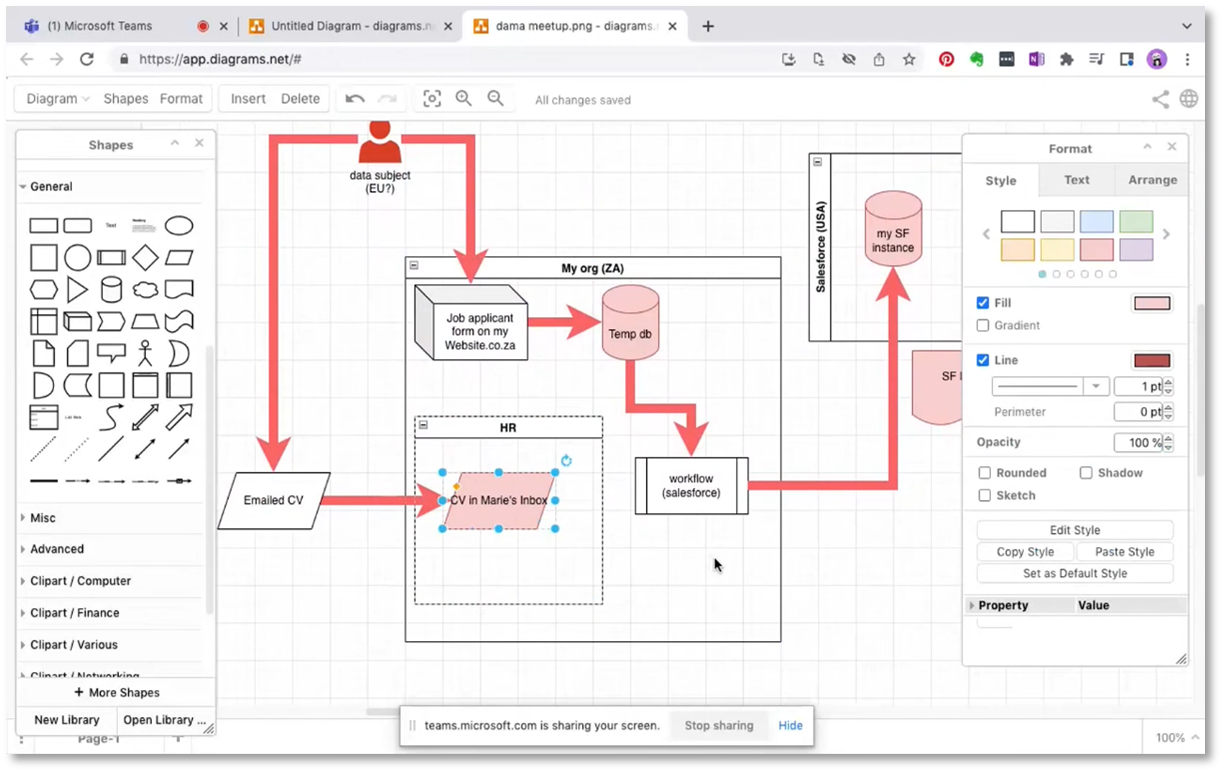
Understanding Data Storage and Management
The webinar emphasises the importance of investigating how long data remains in a specific database, particularly in Salesforce. The need for a contract and retention policy for this data is discussed. Caroline discusses the data flow, including job application forms stored in Salesforce and emailed for interviews. She highlights potential security issues with email, particularly sharing an inbox. Finally, she suggests that structured data, such as that in a database, is more organised and secure, while unstructured data, like emails, can be messy and harder to manage.
Figure 13 Understanding Data Storage and Management
Figure 14 Understanding Data Storage and Management continued.
Importance of Structured Data and Data Visualization in Business
Proper data management is essential for businesses to streamline operations and make informed decisions. Structured data management is a key aspect of this process, involving organising and controlling information systematically. Popular tools for structured data management include Sharepoint and Google, but the effectiveness of these tools depends on individual preferences.
Structured data is entered into a controlled interface, facilitating easy information retrieval. On the other hand, unstructured data, such as in a document, lacks organisation, which makes it difficult to locate specific data. It needs to be translated into structured data to analyse research data collected through paper surveys.
Visualising data flows in a graphical format helps employees understand information flow and identify potential risks. Colour-coded lines can be added to illustrate risk levels or data types, which enhance understanding and facilitate future improvement projects. Managing structured data is crucial for businesses to organise and control information and efficiently make data-driven decisions.
Importance of Language and Data Management in the Workplace
Caroline highlights the importance of language in effective communication for data management. She emphasises the need for users to be comfortable with the language used in the workflow. Managers should access and review data during the interview stage, often printing and downloading it onto their computers for convenience. Strategies must adapt to accommodate paper copies, emphasising proper paper management, including secure disposal of sensitive documents. Risks can be identified by analysing data flow diagrams, and focusing on the most critical risks is essential in data management. Additionally, privacy measures can be implemented, such as not leaving sensitive documents on meeting room tables.
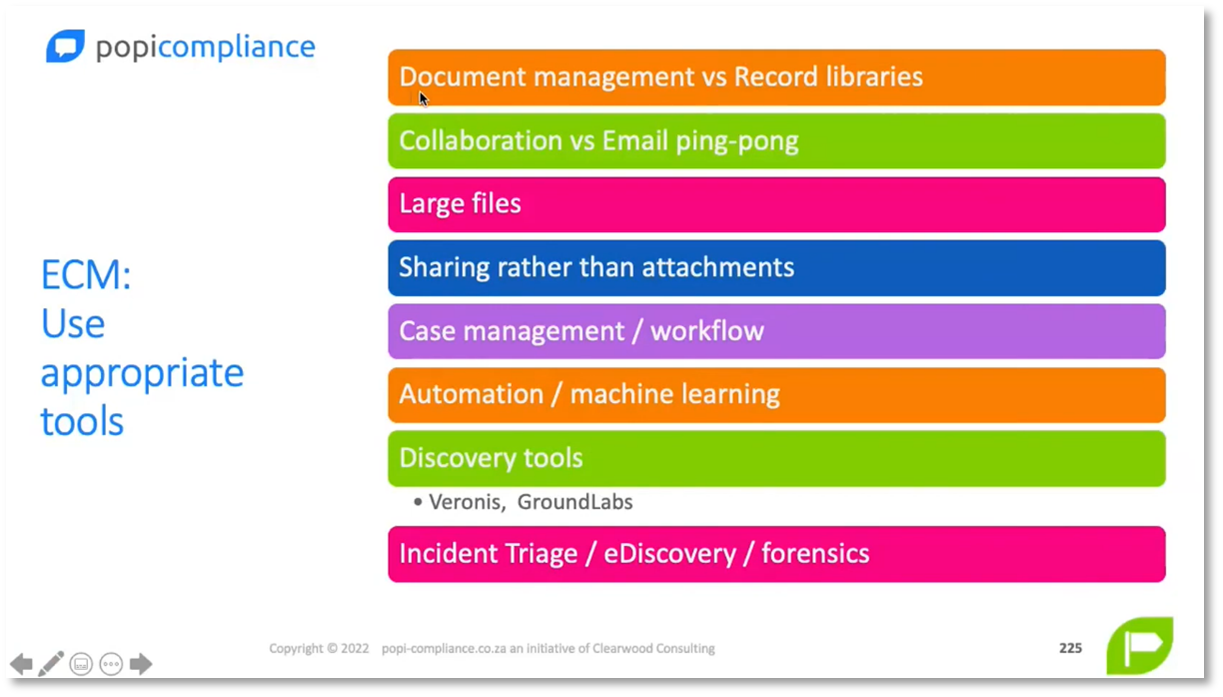
Importance of Data Governance and Tools in Content Management
Establishing effective data governance is critical for businesses today. This requires proper documentation and maintenance of data lineage, flow, and catalogues. Visualisation tools can help in understanding complex data management concepts. However, finding comprehensive tools for managing business processes and lineage can be challenging. Therefore, it is important to prioritise addressing the most significant risks and involving the business in managing them. When choosing enterprise content management tools such as SharePoint, it is crucial to make wise decisions. Consistency in file plans is vital for both physical and electronic records management. Encouraging collaboration tools can help minimise email communication while considering alternative methods for sharing large files, and specific content management requirements, such as asset management tools, can also be beneficial.
Figure 15 ECM: Use appropriate tools
Importance of Case Management and Workflow Tools in Business Operations
Efficient management and sharing of information is crucial for any organisation. Case management and workflow tools are essential in this regard. Implementing case management workflows allows documents and tasks to be organised and shared effectively within a company's SharePoint or website. Using email instead of case management tools can reduce efficiency by up to 60% and increase turnaround time. Organisations can also benefit from automation and machine learning for high-volume, low-complexity processes like invoice management. Additionally, discovery tools such as Ground Labs help identify and manage sensitive data, reducing risks and ensuring compliance. These tools are critical in finding personal information, including details about children, birth dates, gender, and health records.
Importance of Data Management and Tools for Incident Management and Compliance
Microsoft compliance tools are crucial for managing data breaches and incidents effectively. By using discovery tools, businesses can triage the situation and produce reports in case of a breach. Understanding e-discovery and how to preserve evidence for forensic purposes is important. Incorporating data management into incident management, data breach management, and business continuity processes is essential. Using the right tools for structured and unstructured data can also help avoid complications and time constraints. Businesses should pay close attention to technology to prevent the loss and dispersion of structured data. It is also recommended to restrict certain tools, such as Outlook, to prevent unauthorised access and data leakage. Remote desktops should be used to access sensitive data instead of storing it locally. Finally, avoiding accessing sensitive data via personal devices is essential without proper security measures.
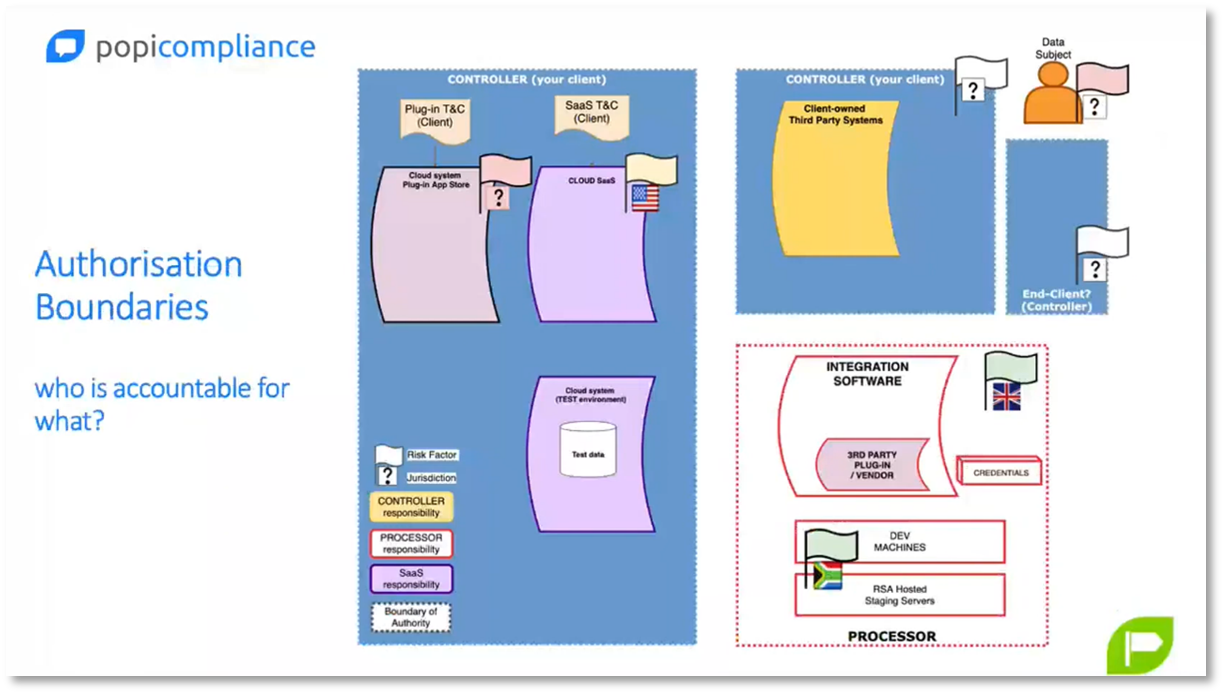
Quick playbook for file shares
When managing file shares that contain sensitive data, it is important to follow certain guidelines to ensure compliance and minimise risks. Firstly, it is best to trust HR's designations and avoid reviewing every document. Secondly, delete anything older than ten years, as there are rarely legislations that require you to keep it longer. Additionally, assign a risk rating to each folder or directory to know the potential penalties and the worth of the data. Be aware of sensitive data, such as bank account details and potential offences and penalties. Finally, consider the risk factors, jurisdiction, responsible parties, and processors in software integrations or document flows. By following these guidelines, you can safeguard your data and avoid potential legal and reputational consequences.
Figure 16 File shares - the Playbook to reduce your risk
Figure 17 Authorisation Boundaries
Managing Privacy Risks with Data Flow Diagrams
The webinar outlines the responsibilities of software users and developers in managing credentials and data flow. Developers use colour coding to assign responsibility for different elements of data flow, with red arrows indicating the responsibility of the processor and yellow indicating the controller's responsibility. Encryption and secure channels for outgoing data are the responsibility of the developer. Red blocks with SPI denote sensitive data, and identifying responsible parties can simplify accountability and reduce privacy risks. Privacy Enabling Technologies (PIT) such as obfuscation or data transfer can help eliminate privacy risks. Data flow diagrams provide insight into complex architectures and metadata while highlighting privacy challenges. Effective communication with stakeholders is crucial for addressing challenges and ensuring accountability.
Effective Communication and Simplified Diagrams
Effective communication requires using simple and relatable visuals, such as basic flowcharts, instead of complex diagrams or special symbols. Colour coding, specifically red for risk, can aid in conveying important information. Making information easy to comprehend and engaging makes people more likely to participate in discussions and understand unfamiliar concepts. Breaking down processes and discussing specific elements, such as third-party contracts, can raise awareness and improve knowledge about a topic.
Tips for Communicating Complex Concepts
To effectively communicate complex ideas, it is often better to use visual aids rather than verbal explanations. Focusing on specific elements of the visual aids, such as colour, can enhance understanding. When working with unstructured data, it's important to use unstructured methodologies. Additionally, a people-oriented approach is crucial when communicating complex ideas.